Question 1
You are assigning VLANs to the ports of switch R1. What VLAN number value is an assigned to the default VLAN?
A VLAN 1003
B. VLAN 1
C. VLAN ON
D. VLAN A
E. VLAN 0
Answer: B
Question 2
What is a characteristic of a static VLAN membership assignment?
A. VMPS server lookup is required
B. Easy to configure
C. Ease of adds, moves, and changes
D. Based on MAC address of the connected device
Answer: B
Explanation
There are two types of VLAN membership assignment:
* Static VLAN: switch ports are assigned to specific VLANs manually
* Dynamic VLAN: switch automatically assigns the port to a VLAN using information from the user device like MAC address, IP address etc. When a device is connected to a switch port, the switch must, in effect, query a database to establish VLAN membership.
Static VLAN assignment provides a simple way to assign VLAN to a port while Dynamic VLANs allow a great deal of flexibility and mobility for end users but require more administrative overhead.
Question 3
What is a characteristic of multi-VLAN access ports?
A. The port has to support STP PortFast.
B. The auxiliary VLAN is for data service and is identified by the PVID.
C. The port hardware is set as an 802.1Q trunk.
D. Both the voice service and data service use the same trust boundary.
Answer: C
Explanation
The multi-VLAN port feature on the Catalyst 2900 XL/3500 XL switches allows for configuring a single port in two or more VLANs. This feature allows users from different VLANs to access a server or router without implementing InterVLAN routing capability. A multi-VLAN port performs normal switching functions in all its assigned VLANs. VLAN traffic on the multi-VLAN port is not encapsulated as it is in trunking -> The port is set as an 802.1Q trunk -> C is correct.
Note: The limitations of implementing multi-VLAN port features are listed below.
1) You cannot configure a multi-VLAN port when a trunk is configured on the switch. You must connect the multi-VLAN port only to a router or server. The switch automatically transitions to VTP transparent mode when the multi-VLAN port feature is enabled, making the VTP disabled.
2) The multi-VLAN port feature is supported only on the Catalyst 2900 XL/3500 XL series switches. This feature is not supported on the Catalyst 4000/5000/6000 series or any other Cisco Catalyst switches.
The following example shows how to configure a port for multi-VLAN mode:
Switch(config-if)# switchport mode multi
The following example shows how to assign a multi-VLAN port already in multi mode to a range of VLANs:
Switch(config-if)# switchport multi vlan 5-10
Question 4
The Company LAN switches are being configured to support the use of Dynamic VLANs. Which of the following are true of dynamic VLAN membership? (Choose two)
A. VLAN membership of a user always remains the same even when he/she is moved to another location.
B. VLAN membership of a user always changes when he/she is moved to another location.
C. Membership can be static or dynamic.
D. Membership can be static only.
Answer: A C
Question 5
Which of the following technologies would an Internet Service Provider use to support overlapping customer VLAN ID’s over transparent LAN services?
A. 802.1q tunneling
B. ATM
C. SDH
D. IP Over Optical Networking
E. ISL
Answer: A
Explanation
Using the IEEE 802.1Q tunneling (QinQ) feature, service providers can use a single VLAN to support customers who have multiple VLANs. The trick here is instead of removing the VLAN tag received from customers, the ISP’s edge switch puts that traffic into the VLAN assigned to that port and adds another VLAN tag outside that tag. Let’s see an example:
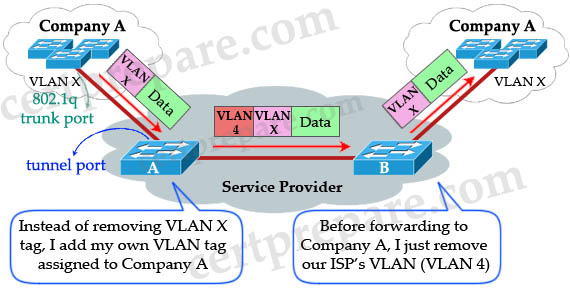 When Switch A (of the Service Provider) receives customer traffic from an 802.1Q trunk port, it does not strip the received 802.1Q tag from the frame header; instead, the tunnel port leaves the 802.1Q tag intact, adds a 1-byte Ethertype field (0×8100) and a 1-byte length field and puts the received customer traffic into the VLAN to which the tunnel port is assigned. This Ethertype 0×8100 traffic, with the received 802.1Q tag intact, is called tunnel traffic. Notice that “VLAN X” here can be one or multiple VLANs, all will be tagged with VLAN 4 (suppose VLAN 4 is assigned to Company A).
When Switch A (of the Service Provider) receives customer traffic from an 802.1Q trunk port, it does not strip the received 802.1Q tag from the frame header; instead, the tunnel port leaves the 802.1Q tag intact, adds a 1-byte Ethertype field (0×8100) and a 1-byte length field and puts the received customer traffic into the VLAN to which the tunnel port is assigned. This Ethertype 0×8100 traffic, with the received 802.1Q tag intact, is called tunnel traffic. Notice that “VLAN X” here can be one or multiple VLANs, all will be tagged with VLAN 4 (suppose VLAN 4 is assigned to Company A).
A benefit of 802.1qQ tunneling is multiple companies can use the overlapped VLANs. For example, Company A can use VLANs 1 to 100 while Company B can use VLANs 50 to 100 (overlapped from VLANs 50 to 100). The ISP’s switches can still classify them because they are attached to different outer VLAN tags. In the example above Company A is assigned to VLAN 4 so we can assign Company B to VLAN 5, Company C to VLAN 6 and so on.
The link between the 802.1Q trunk port on a customer device and the tunnel port is called an asymmetrical link because one end is configured as an 802.1Q trunk port and the other end is configured as a tunnel port.
Note: By default, the native VLAN traffic of a dot1q trunk is sent untagged, which cannot be double-tagged in the service provider network. Because of this situation, the native VLAN traffic might not be tunneled correctly. Be sure that the native VLAN traffic is always sent tagged in an asymmetrical link. To tag the native VLAN egress traffic and drop all untagged ingress traffic, enter the global vlan dot1q tag native command.
Question 6
Static VLANs are being used on the Company network. What is true about static VLANs?
A. Devices use DHCP to request their VLAN.
B. Attached devices are unaware of any VLANs.
C. Devices are assigned to VLANs based on their MAC addresses,
D. Devices are in the same VLAN regardless of which port they attach to.
Answer: B
Explanation
The VLAN tags are only added/removed at the switches. Attached devices are unaware of the existence of VLAN in the network.
Question 7
The Company LAN switches are being configured to support the use of Dynamic VLANs. What should be considered when implementing a dynamic VLAN solution? (Choose two)
A. Each switch port is assigned to a specific VLAN.
B. Dynamic VLANs require a VLAN Membership Policy Server.
C. Devices are in the same VLAN regardless of which port they attach to.
D. Dynamic VLAN assignments are made through the command line interface.
Answer: B C
Explanation
Dynamic VLANs provide membership based on the MAC address of an end-user device. When a device is connected to a switch port, the switch must, in effect, query a database to establish VLAN membership. A network administrator also must assign the user’s MAC address to a VLAN in the database of a VLAN Membership Policy Server (VMPS) -> B is correct.
When the link comes up, the switch does not forward traffic to or from this port until the port is assigned to a VLAN. The source MAC address from the first packet of a new host on the dynamic port is sent to the VMPS, which attempts to match the MAC address to a VLAN in the VMPS database. If there is a match, the VMPS sends the VLAN number for that port. If there is no match, the VMPS either denies the request or shuts down the port (depending on the VMPS secure mode setting) -> Devices are in the same VLAN regardless of which port they attach to -> C is correct.
Question 8
The Company LAN is becoming saturated with broadcasts and multicast traffic. What could you do to help a network with many multicasts and broadcasts?
A. Creating smaller broadcast domains by implementing VLANs.
B. Separate nodes into different hubs.
C. Creating larger broadcast domains by implementing VLANs.
D. Separate nodes into different switches.
E. All of the above.
Answer: A
Explanation
By default, switches flood multicasts out all ports (same as broadcasts). However, many switches and routers can be configured to support multicast traffic, and that support is based on the network addresses uses by multicasts. By implementing VLANs, broadcasts and multicast traffic are only sent to ports in the same VLAN of the sending device.
Question 9
You have just created a new VLAN on your network. What is one step that you should include in your VLAN based implementation and verification plan?
A. Verify that different native VLANs exist between two switches for security purposes,
B. Verify that the VLAN was added on all switches with the use of the show vlan command.
C. Verify that the switch is configured to allow for trunking on the switch ports,
D. Verify that each switch port has the correct IP address space assigned to it for the new VLAN.
Answer: B
Explanation
Different native VLANs will cause error messages about the mismatch, and the potential exists that traffic will not pass correctly between the two native VLANs (although a trunk can be brought up with different native VLANs on each end) -> A is not correct.
Answer C is reasonable but it should be done after configuring trunking, not creating a new VLAN -> C is not correct.
A layer 2 switch only needs one IP address for management purpose -> D is not correct.
Answer B is the best choice to verify if our new VLAN was created, and which ports are associated with it.
Question 10
You have configured a Cisco Catalyst switch to perform Layer 3 routing via an SVI and have assigned that interface to VLAN 20. To check the status of the SVI, you issue the show interfaces vlan 20 command at the CLI prompt. You see from the output display that the interface is in an “up/up” state. What must be true in an SVI configuration to bring the VLAN and line protocol up?
A. The port must be physically connected to another Layer 3 device.
B. At least one port in VLAN 20 must be active.
C. The Layer 3 routing protocol must be operational and receiving routing updates from neighboring peer devices.
D. Because this is a virtual interface, the operational status will always be in an “up/up” state.
Answer: B
Explanation
To be “up/up,” a router VLAN interface must fulfill the following general conditions:
* The VLAN exists and is “active” on the VLAN database of the switch.
* The VLAN interface exists on the router and is not administratively down.
* At least one Layer 2 (access port or trunk) port exists, has a link “up” on this VLAN and is in spanning-tree forwarding state on the VLAN.
Let’s see an example of configuring Switch Virtual Interface (SVI) to perform interVLAN routing between PC0 & PC1:
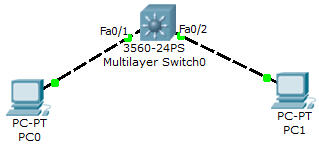 Configuration
Configuration
//Create two VLANs
L3Switch(config)#vlan 10
L3Switch(config-vlan)#vlan 20
L3Switch(config-vlan)#exit
L3Switch(config)#interface fa0/1
L3Switch(config-if)#switchport mode access
L3Switch(config-if)#switchport access vlan 10
L3Switch(config)#interface fa0/2
L3Switch(config-if)#switchport mode access
L3Switch(config-if)#switchport access vlan 20
L3Switch(config-if)#exit
//Enable IP routing on this Layer 3 Switch
L3Switch(config)#ip routing
//Create two SVIs for interVLAN routing:
L3Switch(config)#interface vlan 10
L3Switch(config-if)#ip address 10.0.0.1 255.255.255.0
L3Switch(config)#interface vlan 20
L3Switch(config-if)#ip address 20.0.0.1 255.255.255.0
On PC0, assign the IP address 10.0.0.2 255.255.255.0 and the default gateway: 10.0.0.1
On PC1, assign the IP address 20.0.0.2 255.255.255.0 and the default gateway: 20.0.0.1
Now we can ping from PC0 to PC1:
PC0>ping 20.0.0.2
Pinging 20.0.0.2 with 32 bytes of data:
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Question 11
Refer to the exhibit. Based upon the output of show vlan on switch CAT2, what can we conclude about interfaces Fa0/13 and Fa0/14?
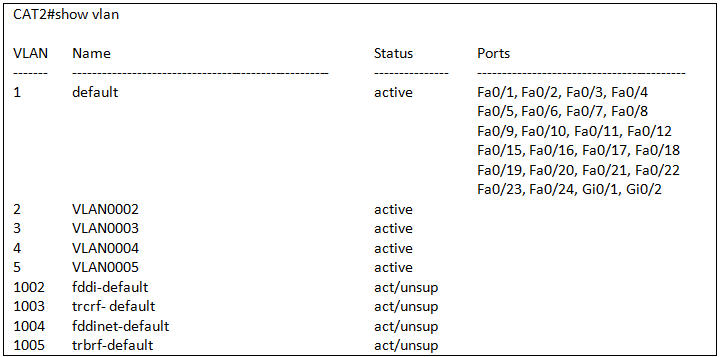
A. That interfaces Fa0/13 and Fa0/14 are in VLAN 1
B. That interfaces Fa0/13 and Fa0/14 are down
C. That interfaces Fa0/13 and Fa0/14 are trunk interfaces
D. That interfaces Fa0/13 and Fa0/14 have a domain mismatch with another switch
E. That interfaces Fa0/13 and Fa0/14 have a duplex mismatch with another switch
Answer: C
Explanation
Trunk ports are part of multiple VLANs, not of just a single VLAN so they never show up in the show vlan command. You can check the trunk port with the show interfaces trunk or show interface {port} switchport command.
Note: Trunk ports that are not connected appear by default in vlan 1 and also appear in the output of the show vlan command.
Question 12
What two pieces of information will the show vlan id 5 command display? (Choose two)
A. Ports in VLAN 5
B. Utilization
C. VLAN information on port 0/5
D. Filters
E. MTU and type
Answer: A E
Explanation
The show vlan id vlan-id command display information about a particular VLAN. But notice that this command will also list trunk ports that allow this VLAN to run on. An example of the “show vlan id” command is shown below:
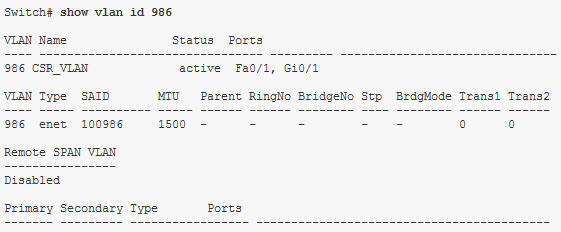
Question 13
What are some virtues of implementing end-to-end VLANs? (Choose two)
A. End-to-end VLANs are easy to manage.
B. Users are grouped into VLANs independent of a physical location.
C. Each VLAN has a common set of security and resource requirements for all members.
D. Resources are restricted to a single location.
Answer: B C
Explanation
There are two kinds of VLANs:
* End-to-end VLANs: also called campuswide VLANs, span the entire switch fabric of a network. They are positioned to support maximum flexibility and mobility of end devices. Users can be assigned to VLANs regardless of their physical location. As a user moves around the campus, that user’s VLAN membership stays the same. End-to-end VLANs should group users according to common requirements. All users in a VLAN should have roughly the same traffic flow patterns
* Local VLANs: based on geographic locations by demarcation at a hierarchical boundary (core, distribution, access)
(Reference: CCNP SWITCH 642-813 Official Certification Guide)
Question 14
Which two statements are true about a switched virtual interface (SVI)? (Choose two)
A. An SVI is created by entering the no switchport command in interface configuration mode.
B. An SVI is normally created for the default VLAN (VLAN1) to permit remote switch administration.
C. An SVI provides a default gateway for a VLAN.
D. Multiple SVIs can be associated with a VLAN.
E. SVI is another name for a routed port.
Answer: B C
Explanation
Catalyst L2 fixed configuration switches that run Cisco IOS Software have only one configurable IP management interface, which by default is interface VLAN 1. Pure layer 2 switches can have only one interface VLAN up at the time. This is called the management VLAN (in IOS) or the sc0 interface (in CatOS). The main purpose of this interface is management (telnet, SNMP, etc). If the switch is a Layer 3 switch, you can configure multiple VLANs and route between them. An L3 switch can handle multiple IPs, so there is no specific management VLAN on the switch.
Question 15
You have just created a new VLAN on your network. What is one step that you should include in your VLAN based implementation and verification plan?
A. Verify that trunked links are configured to allow the VLAN traffic.
B. Verify that the switch is configured to allow for trunking on the switch ports.
C. Verify that each switch port has the correct IP address space assigned to it for the new VLAN.
D. Verify that different native VLANs exist between two switches for security purposes.
Answer: A
Explanation
A VLAN-based implementation and verification plan should include:
* Verification that trunked links are configured to allow the newly created VLANs.
* Verification that the SVI has already been created and that it shows up on all required switches using the show vlan command.
Question 16
You have just created a new VLAN on your network for inter-VLAN routing. What is one step that you should include in your VLAN-based implementation and verification plan?
A. Verify that different native VLANs exist between two switches for security purposes.
B. Verify that the switch is configured to allow for trunking on the switch ports.
C. Verify that each switch port has the proper IP address space assigned to it for the new VLAN.
D. Verify that the VLAN virtual interface has been correctly created and enabled.
Answer: D
Question 17
Under what circumstances should an administrator prefer local VLANs over end-to-end VLANs?
A. Eighty percent of traffic on the network is destined for Internet sites.
B. There are common sets of traffic filtering requirements for workgroups located in multiple buildings.
C. Eighty percent of a workgroup’s traffic is to the workgroup’s own local server.
D. Users are grouped into VLANs independent of physical location.
Answer: A
Explanation
End-to-end VLAN follows the 80/20 rule in which 80 percent of user traffic stays within the local workgroup, whereas 20 percent is destined for a remote resource in the campus network (like Internet…).
In contrast to end-to-end-VLAN, local VLAN follows the 20/80 rule: only 20 percent of traffic is local, whereas 80 percent is destined to a remote re-source across the core layer -> A is correct.
Question 18
Which of the following statements is true about the 80/20 rule (Choose two)?
A. 20 percent of the traffic on a network segment should be local.
B. no more than 20 percent of the network traffic should be able to move across a backbone.
C. no more than 80 percent of the network traffic should be able to move across a backbone.
D. 80 percent of the traffic on a network segment should be local.
Answer: B D
Explanation
The 80/20 rule states that 80 percent of user traffic stays within the local workgroup, whereas 20 percent is destined for a remote resource in the campus network
Question 19
Which two statements are true about best practices in VLAN design? (Choose two.)
A. Routing should occur at the access layer if voice VLANs are utilized. Otherwise, routing should occur at the distribution layer.
B. Routing may be performed at all layers but is most commonly done at the core and distribution layers.
C. Routing should not be performed between VLANs located on separate switches.
D. VLANs should be local to a switch.
E. VLANs should be localized to a single switch unless voice VLANs are being utilized.
Answer: B D
Explanation
First let’s review main characteristics of three layers in a campus network:
* Access layer:
+ Low cost per switch port
+ High port density
+ Scalable uplinks to higher layers
+ User access functions such as VLAN membership, traffic and protocol filtering, and quality of service (QoS)
+ Resiliency through multiple uplinks
* Distribution Layer:
+ Aggregation of multiple access-layer devices
+ High Layer 3 throughput for packet handling
+ Security and policy-based connectivity functions through access lists or packet filters
+ QoS features
+ Scalable and resilient high-speed links to the core and access layers
* Core layer:
+ Very high throughput at Layer 3
+ No costly or unnecessary packet manipulations (access lists, packet filtering)
+ Redundancy and resilience for high availability
+ Advanced QoS functions
We can see at Distribution and Core layers, Layer 3 throughput (routing) is very high -> B is correct.
Nowadays, end-to-end VLANs are not recommended in an enterprise network, unless there is a good reason. In an end-to-end VLAN, broadcast traffic is carried over from one end of the network to the other, creating the possibility for a broadcast storm or Layer 2 bridging
loop to spread across the whole extent of a VLAN. This can exhaust the bandwidth of distribution and core-layer links, as well as switch CPU resources. Now the storm or loop has disrupted users on the end-to-end VLAN, in addition to users on other VLANs that might
be crossing the core.
When such a problem occurs, troubleshooting becomes more difficult. In other words, the risks of end-to-end VLANs outweigh the convenience and benefits.
From that we can infer VLAN traffic should be local to the switch -> D is correct.
Question 20

Refer to the exhibit. The user who is connected to interface FastEthernet 0/1 is on VLAN 10 and cannot access network resources. On the basis of the information in the exhibit, which command sequence would correct the problem?
A. SW1(config)# vlan 10
SW1(config-vlan)# no shut
B. SW1(config)# interface fastethernet 0/1
SW1(config-if)# switchport mode access
SW1(config-if)# switchport access vlan 10
C. SW1(config)# interface fastethernet 0/1
SW1(config-if)# switchport mode access
D. SW1(config)# vlan 10
SW1(config-vlan)# state active
E. SW1(config)# interface fastethernet 0/1
SW1(config-if)# no shut
Answer: E
Question 21
Refer to the exhibit. On the basis of the output generated by the show commands, which two statements are true? (Choose two)
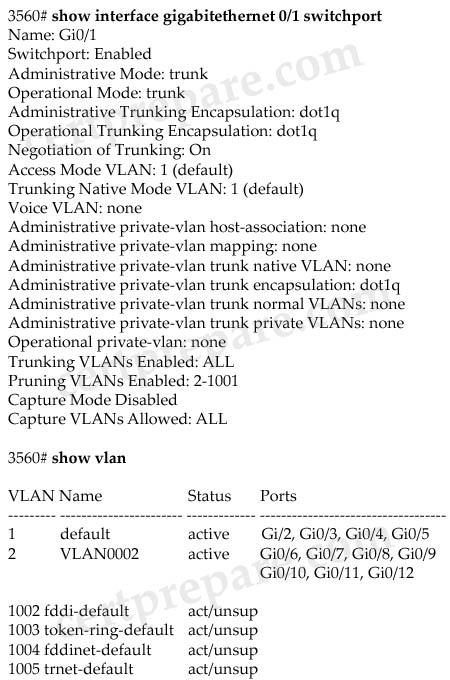
A. Interface gigabitethernet 0/1 has been configured as Layer 3 ports.
B. Interface gigabitethernet 0/1 does not appear in the show vlan output because switchport is enabled.
C. Interface gigabitethernet 0/1 does not appear in the show vlan output because it is configured as a trunk interface.
D. VLAN2 has been configured as the native VLAN for the 802.1q trunk on interface gigabitethernet 0/1.
E. Traffic on VLAN 1 that is sent out gigabitethernet 0/1 will have an 802.1q header applied.
F. Traffic on VLAN 2 that is sent out gigabitethernet 0/1 will have an 802.1q header applied.
Answer: C F
Explanation
From the output of show interface gigabitethernet 0/1 switchport command we can see this port is currently configured as trunked port (Operational Mode: trunk) and uses 802.1q encapsulation. So surely the “show vlan” command will not list this port -> C is correct.
Also from the first output we learned the native VLAN is VLAN 1 (Trunking Native Mode VLAN:1) so only traffic from this VLAN is sent untagged -> traffic sent from VLAN 2 out this port will have an 802.1q header applied -> F is correct.
Question 22
When you issue a command show port 3/1 on an Ethernet port, you observe the ‘Giants’ column has a non-zero entry. What could cause of this?
A. IEEE 802.1Q
B. IEEE 802.10
C. Misconfigured NIC
D. User configuration
E. All of the above
Answer: A
Explanation
Generally, frames that are greater than 1522 bytes are categorized as giant frames (notice that a normal Ethernet frame has a size that ranges from 64 bytes to 1518 bytes). Giant frames often are the result of some protocol-tagging mechanisms, for example 802.1Q frames (1522 bytes), MPLS (1518 + 4 * n, where n is the number of stacked labels), ISL frames (1548 bytes).
There are nothing wrong with giant frames, just make sure you configure both end devices to support these frames.
Note: In fact, frames that are created by 802.1Q are often known as baby giants (frames that are slightly larger than 1518 bytes).
Question 23
You want to configure a switched internetwork with multiple VLANs as shown above. Which of the following commands should you issue on SwitchA for the port connected to SwitchB?
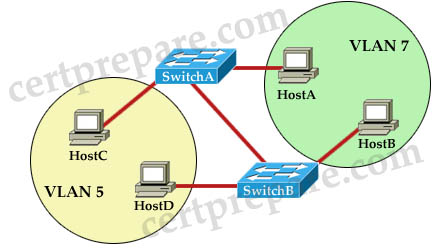 A. switchport mode trunk
A. switchport mode trunk
B. switchport access vlan 5
C. switchport mode access vlan 5
D. switchport trunk native vlan 5
Answer: A
Explanation
To support interVLAN routing, the links between two switches must be configured as trunk link.
Question 24
Refer to the exhibit. VLAN 1 and VLAN 2 are configured on the trunked links between Switch A and Switch B. Port Fa 0/2 on Switch B is currently in a blocking state for both VLANs. What should be done to load balance VLAN traffic between Switch A and Switch B?

A. Lower the port priority for VLAN 1 on port 0/1 for Switch A.
B. Lower the port priority for VLAN 1 on port 0/2 for Switch A.
C. Make the bridge ID of Switch B lower than the ID of Switch A.
D. Enable HSRP on the access ports.
Answer: B
Explanation
In general, lower the port priority for VLAN 1 will lower the Root Bridge ID for port Fa0/2 on Switch A -> traffic for VLAN 1 will flow via Fa0/2 link.
Question 25
On a multilayer Catalyst switch, which interface command is used to convert a Layer 3 interface to a Layer 2 interface?
A. switchport access vlan vlan-id
B. switchport
C. switchport mode access
D. no switchport
Answer: B
Question 26
Refer to the exhibit and the show interfaces fastethernet0/1 switchport outputs. Users in VLAN 5 on switch SW_A complain that they do not have connectivity to the users in VLAN 5 on switch SW_B. What should be done to fix the problem?
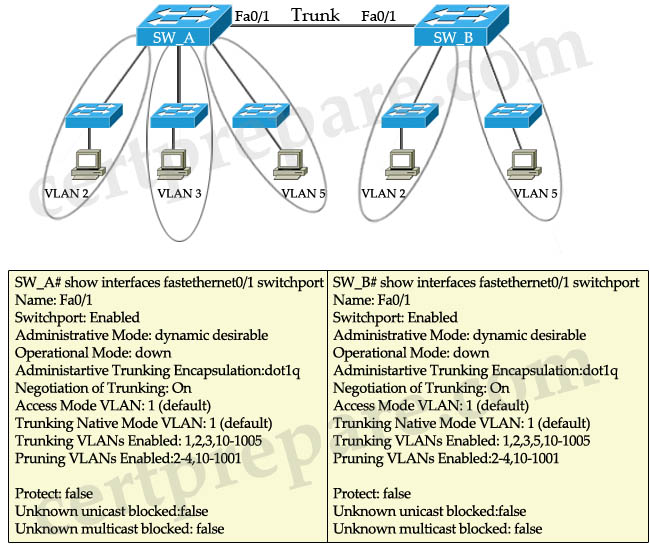 A. Configure the same number of VLANs on both switches.
A. Configure the same number of VLANs on both switches.
B. Create switch virtual interfaces (SVI) on both switches to route the traffic.
C. Define VLAN 5 in the allowed list for the trunk port on SW_A.
D. Disable pruning for all VLANs in both switches.
E. Define VLAN 5 in the allowed list for the trunk port on SW_B.
Answer: C
Explanation
SW_A is missing VLAN 5 in the “Trunking VLANs Enabled”, that means the trunk link currently does not accept traffic from VLAN 5 to be sent on the link.
Question 27
Refer to the show interface Gi0/1 switchport command output shown in the exhibit. Which two statements are true about this interface? (Choose two)

A. This interface is a member of a voice VLAN.
B. This interface is configured for access mode.
C. This interface is a dot1q trunk passing all configured VLANs.
D. This interface is a member of VLAN 7.
E. This interface is a member of VLAN 1.
Answer: B D
Question 28
In the three-layer hierarchical network design model; what’s associated with the access layer? (Choose two)
A. optimized transport structure
B. high port density
C. boundary definition
D. data encryption
E. local VLANs
F. route summaries
Answer: B E
Explanation
Main characteristics of three layers in the three-layer hierarchical network design model:
* Access layer:
+ Low cost per switch port
+ High port density
+ Scalable uplinks to higher layers
+ User access functions such as VLAN membership, traffic and protocol filtering, and quality of service (QoS)
+ Resiliency through multiple uplinks
* Distribution Layer:
+ Aggregation of multiple access-layer devices
+ High Layer 3 throughput for packet handling
+ Security and policy-based connectivity functions through access lists or packet filters
+ QoS features
+ Scalable and resilient high-speed links to the core and access layers
* Core layer:
+ Very high throughput at Layer 3
+ No costly or unnecessary packet manipulations (access lists, packet filtering)
+ Redundancy and resilience for high availability
+ Advanced QoS functions
Also, end-to-end VLANs and local VLANs belong to access layer.
Question 29
Refer to the following exhibits:
Exhibit #1

Exhibit #2

Study the exhibits carefully. The switchport output in Exhibit #1 displays the default settings of interface FastEthernet 0/13 on switch Sw1. Figure 2 displays the desired interface settings. Which command sequence would configure interface FastEthernet 0/13 as displayed in Exhibit #2?
A.
Sw1(config-if)# switchport trunk encapsulation dot1q
Sw1 (config-if)# switchport mode dynamic auto
Sw1 (config-if)# switchport trunk native DATA
Sw1 (config-if)# switchport trunk allowed vlan add 1,10,20
B.
Sw1(config-if)# switchport trunk encapsulation dot1q
Sw1(config-if)# switchport mode dynamic desirable
Sw1(config-if)# switchport trunk native vlan DATA
Sw1(config-if)# switchport trunk allowed vlan 1,10,20
C.
Sw1 (config-if)# switchport trunk encapsulation dot1q
Sw1 (config-if)# switchport mode trunk
Sw1 (config-if)# switchport trunk native DATA
Sw1 (config-if)# switchport trunk allowed vlan 1,10,20
D.
Sw1(config-if)# switchport trunk encapsulation dot1q
Sw1(config-if)#switchport mode dynamic desirable
Sw1(config-if)#switchport trunk native vlan 10
E.
Sw1 (config-if)# switchport trunk encapsulation dot1q
Sw1 (config-if)# switchport mode dynamic desirable
Sw1 (config-if)# switchport trunk native vlan 10
Sw1 (config-if)# switchport trunk allowed vlan 1,10,20
Answer: E
Question 30
What is the result of these commands?
A. Two new vlans are created on six switch ports
B. One new vlan is created on five switch ports
C. Six new vlans are created on six switch ports
D. One new vlan is created with the vlan number 2
Answer: D
Explanation
If the administrator has not created VLAN 2 before typing this command, a message will appear informing that VLAN 2 is created automatically.
Question 31
Which three statements apply to access control of both bridged and routed traffic for VLANs? (Choose three)
A. Router ACLs can be applied to the input and output directions of a VLAN interface
B. Bridged ACLs can be applied to the input and output directions of a VLAN interface
C. Only router ACLs can be applied to a VLAN interface
D. VLAN maps can be applied to a VLAN interface
E. VLAN maps and router ACLs can be used in combination
Answer: A C E
Explanation
Bridged ACL (or VLAN Access-list, or VLAN map) is used to filter traffic that is flowing within a VLAN. It can only be applied to a VLAN, not interface -> C is correct.
An Interface VLAN (or Switch Virtual Interface – SVI) is very similar to a physical interface on a router, although it is a virtual interface only. We can apply Router ACL to the inbound and outbound direction of a VLAN interface -> A is correct.
To apply access control to both bridged and routed traffic, you can use VACLs alone or a combination of VACLs and ACLs. You can define ACLs on the VLAN interfaces to apply access control to both the ingress and egress routed traffic. You can define a VACL to apply access control to the bridged traffic. -> E is correct.
Note: In CCNA we learned about Access list, in fact it is Router Access list.
Question 32
When you create a network implementation for a VLAN solution, what is one procedure that you should include in your plan?
A. Perform an incremental implementation of components.
B. Implement the entire solution and then test end-to-end to make sure that it is performing as designed.
C. Implement trunking of all VLANs to ensure that traffic is crossing the network as needed before performing any pruning of VLANs.
D. Test the solution on the production network in off hours.
Answer: A
Question 33
Two switches SA and SB are connected as shown below. Given the below partial configuration, which two statements are true about VLAN traffic? (Choose two)
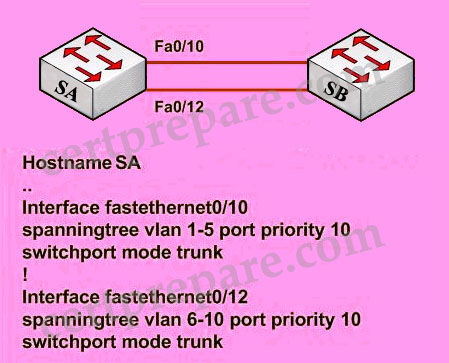
A – VLANs 1-5 will be blocked if fa0/10 goes down.
B – VLANs 6-10 have a port priority of 128 on fa0/10.
C – VLANs 6-10 will use fa0/10 as a backup only.
D – VLANs 1-10 are configured to load share between fa0/10 and fa0/12.
Answer: C D
Explanation:
Let’s assume that SA is the root bridge for all VLANs, it will make the explanation a bit clearer…
First we should understand what will happen if nothing is configured (use default values). Because we assumed that SA is the root bridge so all of its ports will forward. SB will need to block one of its ports to avoid a bridging loop between the two switches. But how does SB select its blocked port? Well, the answer is based on the BPDUs it receives from SA. A BPDU is superior than another if it has:
1. A lower Root Bridge ID
2. A lower path cost to the Root
3. A lower Sending Bridge ID
4. A lower Sending Port ID
These four parameters are examined in order. In this specific case, all the BPDUs sent by SA have the same Root Bridge ID, the same path cost to the Root and the same Sending Bridge ID. The only parameter left to select the best one is the Sending Port ID (Port ID = port priority + port index). If using default values, the default port priority’s value is 32 or 128 (128 is much more popular today but 32 is also a default port priority’s value), so SB will compare port index values, which are unique to each port on the switch, and because Fa0/12 is inferior to Fa0/10, SB will select the port connected with Fa0/10 (of SA) as its root port and block the other port.
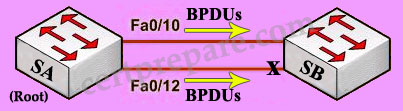
Answer D is correct because this configuration provide load-balance traffic based on VLAN basis. VLANs 1-5 use Fa0/10 and VLANs 6-10 use Fa0/12 as their main paths.
Note: We can not assure the answer B is always correct so we should choose C and D if the question asks us to give only 2 choices).
You are assigning VLANs to the ports of switch R1. What VLAN number value is an assigned to the default VLAN?
A VLAN 1003
B. VLAN 1
C. VLAN ON
D. VLAN A
E. VLAN 0
Answer: B
Question 2
What is a characteristic of a static VLAN membership assignment?
A. VMPS server lookup is required
B. Easy to configure
C. Ease of adds, moves, and changes
D. Based on MAC address of the connected device
Answer: B
Explanation
There are two types of VLAN membership assignment:
* Static VLAN: switch ports are assigned to specific VLANs manually
* Dynamic VLAN: switch automatically assigns the port to a VLAN using information from the user device like MAC address, IP address etc. When a device is connected to a switch port, the switch must, in effect, query a database to establish VLAN membership.
Static VLAN assignment provides a simple way to assign VLAN to a port while Dynamic VLANs allow a great deal of flexibility and mobility for end users but require more administrative overhead.
Question 3
What is a characteristic of multi-VLAN access ports?
A. The port has to support STP PortFast.
B. The auxiliary VLAN is for data service and is identified by the PVID.
C. The port hardware is set as an 802.1Q trunk.
D. Both the voice service and data service use the same trust boundary.
Answer: C
Explanation
The multi-VLAN port feature on the Catalyst 2900 XL/3500 XL switches allows for configuring a single port in two or more VLANs. This feature allows users from different VLANs to access a server or router without implementing InterVLAN routing capability. A multi-VLAN port performs normal switching functions in all its assigned VLANs. VLAN traffic on the multi-VLAN port is not encapsulated as it is in trunking -> The port is set as an 802.1Q trunk -> C is correct.
Note: The limitations of implementing multi-VLAN port features are listed below.
1) You cannot configure a multi-VLAN port when a trunk is configured on the switch. You must connect the multi-VLAN port only to a router or server. The switch automatically transitions to VTP transparent mode when the multi-VLAN port feature is enabled, making the VTP disabled.
2) The multi-VLAN port feature is supported only on the Catalyst 2900 XL/3500 XL series switches. This feature is not supported on the Catalyst 4000/5000/6000 series or any other Cisco Catalyst switches.
The following example shows how to configure a port for multi-VLAN mode:
Switch(config-if)# switchport mode multi
The following example shows how to assign a multi-VLAN port already in multi mode to a range of VLANs:
Switch(config-if)# switchport multi vlan 5-10
Question 4
The Company LAN switches are being configured to support the use of Dynamic VLANs. Which of the following are true of dynamic VLAN membership? (Choose two)
A. VLAN membership of a user always remains the same even when he/she is moved to another location.
B. VLAN membership of a user always changes when he/she is moved to another location.
C. Membership can be static or dynamic.
D. Membership can be static only.
Answer: A C
Question 5
Which of the following technologies would an Internet Service Provider use to support overlapping customer VLAN ID’s over transparent LAN services?
A. 802.1q tunneling
B. ATM
C. SDH
D. IP Over Optical Networking
E. ISL
Answer: A
Explanation
Using the IEEE 802.1Q tunneling (QinQ) feature, service providers can use a single VLAN to support customers who have multiple VLANs. The trick here is instead of removing the VLAN tag received from customers, the ISP’s edge switch puts that traffic into the VLAN assigned to that port and adds another VLAN tag outside that tag. Let’s see an example:

A benefit of 802.1qQ tunneling is multiple companies can use the overlapped VLANs. For example, Company A can use VLANs 1 to 100 while Company B can use VLANs 50 to 100 (overlapped from VLANs 50 to 100). The ISP’s switches can still classify them because they are attached to different outer VLAN tags. In the example above Company A is assigned to VLAN 4 so we can assign Company B to VLAN 5, Company C to VLAN 6 and so on.
The link between the 802.1Q trunk port on a customer device and the tunnel port is called an asymmetrical link because one end is configured as an 802.1Q trunk port and the other end is configured as a tunnel port.
Note: By default, the native VLAN traffic of a dot1q trunk is sent untagged, which cannot be double-tagged in the service provider network. Because of this situation, the native VLAN traffic might not be tunneled correctly. Be sure that the native VLAN traffic is always sent tagged in an asymmetrical link. To tag the native VLAN egress traffic and drop all untagged ingress traffic, enter the global vlan dot1q tag native command.
Question 6
Static VLANs are being used on the Company network. What is true about static VLANs?
A. Devices use DHCP to request their VLAN.
B. Attached devices are unaware of any VLANs.
C. Devices are assigned to VLANs based on their MAC addresses,
D. Devices are in the same VLAN regardless of which port they attach to.
Answer: B
Explanation
The VLAN tags are only added/removed at the switches. Attached devices are unaware of the existence of VLAN in the network.
Question 7
The Company LAN switches are being configured to support the use of Dynamic VLANs. What should be considered when implementing a dynamic VLAN solution? (Choose two)
A. Each switch port is assigned to a specific VLAN.
B. Dynamic VLANs require a VLAN Membership Policy Server.
C. Devices are in the same VLAN regardless of which port they attach to.
D. Dynamic VLAN assignments are made through the command line interface.
Answer: B C
Explanation
Dynamic VLANs provide membership based on the MAC address of an end-user device. When a device is connected to a switch port, the switch must, in effect, query a database to establish VLAN membership. A network administrator also must assign the user’s MAC address to a VLAN in the database of a VLAN Membership Policy Server (VMPS) -> B is correct.
When the link comes up, the switch does not forward traffic to or from this port until the port is assigned to a VLAN. The source MAC address from the first packet of a new host on the dynamic port is sent to the VMPS, which attempts to match the MAC address to a VLAN in the VMPS database. If there is a match, the VMPS sends the VLAN number for that port. If there is no match, the VMPS either denies the request or shuts down the port (depending on the VMPS secure mode setting) -> Devices are in the same VLAN regardless of which port they attach to -> C is correct.
Question 8
The Company LAN is becoming saturated with broadcasts and multicast traffic. What could you do to help a network with many multicasts and broadcasts?
A. Creating smaller broadcast domains by implementing VLANs.
B. Separate nodes into different hubs.
C. Creating larger broadcast domains by implementing VLANs.
D. Separate nodes into different switches.
E. All of the above.
Answer: A
Explanation
By default, switches flood multicasts out all ports (same as broadcasts). However, many switches and routers can be configured to support multicast traffic, and that support is based on the network addresses uses by multicasts. By implementing VLANs, broadcasts and multicast traffic are only sent to ports in the same VLAN of the sending device.
Question 9
You have just created a new VLAN on your network. What is one step that you should include in your VLAN based implementation and verification plan?
A. Verify that different native VLANs exist between two switches for security purposes,
B. Verify that the VLAN was added on all switches with the use of the show vlan command.
C. Verify that the switch is configured to allow for trunking on the switch ports,
D. Verify that each switch port has the correct IP address space assigned to it for the new VLAN.
Answer: B
Explanation
Different native VLANs will cause error messages about the mismatch, and the potential exists that traffic will not pass correctly between the two native VLANs (although a trunk can be brought up with different native VLANs on each end) -> A is not correct.
Answer C is reasonable but it should be done after configuring trunking, not creating a new VLAN -> C is not correct.
A layer 2 switch only needs one IP address for management purpose -> D is not correct.
Answer B is the best choice to verify if our new VLAN was created, and which ports are associated with it.
Question 10
You have configured a Cisco Catalyst switch to perform Layer 3 routing via an SVI and have assigned that interface to VLAN 20. To check the status of the SVI, you issue the show interfaces vlan 20 command at the CLI prompt. You see from the output display that the interface is in an “up/up” state. What must be true in an SVI configuration to bring the VLAN and line protocol up?
A. The port must be physically connected to another Layer 3 device.
B. At least one port in VLAN 20 must be active.
C. The Layer 3 routing protocol must be operational and receiving routing updates from neighboring peer devices.
D. Because this is a virtual interface, the operational status will always be in an “up/up” state.
Answer: B
Explanation
To be “up/up,” a router VLAN interface must fulfill the following general conditions:
* The VLAN exists and is “active” on the VLAN database of the switch.
* The VLAN interface exists on the router and is not administratively down.
* At least one Layer 2 (access port or trunk) port exists, has a link “up” on this VLAN and is in spanning-tree forwarding state on the VLAN.
Let’s see an example of configuring Switch Virtual Interface (SVI) to perform interVLAN routing between PC0 & PC1:

//Create two VLANs
L3Switch(config)#vlan 10
L3Switch(config-vlan)#vlan 20
L3Switch(config-vlan)#exit
L3Switch(config)#interface fa0/1
L3Switch(config-if)#switchport mode access
L3Switch(config-if)#switchport access vlan 10
L3Switch(config)#interface fa0/2
L3Switch(config-if)#switchport mode access
L3Switch(config-if)#switchport access vlan 20
L3Switch(config-if)#exit
//Enable IP routing on this Layer 3 Switch
L3Switch(config)#ip routing
//Create two SVIs for interVLAN routing:
L3Switch(config)#interface vlan 10
L3Switch(config-if)#ip address 10.0.0.1 255.255.255.0
L3Switch(config)#interface vlan 20
L3Switch(config-if)#ip address 20.0.0.1 255.255.255.0
On PC0, assign the IP address 10.0.0.2 255.255.255.0 and the default gateway: 10.0.0.1
On PC1, assign the IP address 20.0.0.2 255.255.255.0 and the default gateway: 20.0.0.1
Now we can ping from PC0 to PC1:
PC0>ping 20.0.0.2
Pinging 20.0.0.2 with 32 bytes of data:
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Reply from 20.0.0.2: bytes=32 time=40ms TTL=127
Question 11
Refer to the exhibit. Based upon the output of show vlan on switch CAT2, what can we conclude about interfaces Fa0/13 and Fa0/14?

A. That interfaces Fa0/13 and Fa0/14 are in VLAN 1
B. That interfaces Fa0/13 and Fa0/14 are down
C. That interfaces Fa0/13 and Fa0/14 are trunk interfaces
D. That interfaces Fa0/13 and Fa0/14 have a domain mismatch with another switch
E. That interfaces Fa0/13 and Fa0/14 have a duplex mismatch with another switch
Answer: C
Explanation
Trunk ports are part of multiple VLANs, not of just a single VLAN so they never show up in the show vlan command. You can check the trunk port with the show interfaces trunk or show interface {port} switchport command.
Note: Trunk ports that are not connected appear by default in vlan 1 and also appear in the output of the show vlan command.
Question 12
What two pieces of information will the show vlan id 5 command display? (Choose two)
A. Ports in VLAN 5
B. Utilization
C. VLAN information on port 0/5
D. Filters
E. MTU and type
Answer: A E
Explanation
The show vlan id vlan-id command display information about a particular VLAN. But notice that this command will also list trunk ports that allow this VLAN to run on. An example of the “show vlan id” command is shown below:

Question 13
What are some virtues of implementing end-to-end VLANs? (Choose two)
A. End-to-end VLANs are easy to manage.
B. Users are grouped into VLANs independent of a physical location.
C. Each VLAN has a common set of security and resource requirements for all members.
D. Resources are restricted to a single location.
Answer: B C
Explanation
There are two kinds of VLANs:
* End-to-end VLANs: also called campuswide VLANs, span the entire switch fabric of a network. They are positioned to support maximum flexibility and mobility of end devices. Users can be assigned to VLANs regardless of their physical location. As a user moves around the campus, that user’s VLAN membership stays the same. End-to-end VLANs should group users according to common requirements. All users in a VLAN should have roughly the same traffic flow patterns
* Local VLANs: based on geographic locations by demarcation at a hierarchical boundary (core, distribution, access)
(Reference: CCNP SWITCH 642-813 Official Certification Guide)
Question 14
Which two statements are true about a switched virtual interface (SVI)? (Choose two)
A. An SVI is created by entering the no switchport command in interface configuration mode.
B. An SVI is normally created for the default VLAN (VLAN1) to permit remote switch administration.
C. An SVI provides a default gateway for a VLAN.
D. Multiple SVIs can be associated with a VLAN.
E. SVI is another name for a routed port.
Answer: B C
Explanation
Catalyst L2 fixed configuration switches that run Cisco IOS Software have only one configurable IP management interface, which by default is interface VLAN 1. Pure layer 2 switches can have only one interface VLAN up at the time. This is called the management VLAN (in IOS) or the sc0 interface (in CatOS). The main purpose of this interface is management (telnet, SNMP, etc). If the switch is a Layer 3 switch, you can configure multiple VLANs and route between them. An L3 switch can handle multiple IPs, so there is no specific management VLAN on the switch.
Question 15
You have just created a new VLAN on your network. What is one step that you should include in your VLAN based implementation and verification plan?
A. Verify that trunked links are configured to allow the VLAN traffic.
B. Verify that the switch is configured to allow for trunking on the switch ports.
C. Verify that each switch port has the correct IP address space assigned to it for the new VLAN.
D. Verify that different native VLANs exist between two switches for security purposes.
Answer: A
Explanation
A VLAN-based implementation and verification plan should include:
* Verification that trunked links are configured to allow the newly created VLANs.
* Verification that the SVI has already been created and that it shows up on all required switches using the show vlan command.
Question 16
You have just created a new VLAN on your network for inter-VLAN routing. What is one step that you should include in your VLAN-based implementation and verification plan?
A. Verify that different native VLANs exist between two switches for security purposes.
B. Verify that the switch is configured to allow for trunking on the switch ports.
C. Verify that each switch port has the proper IP address space assigned to it for the new VLAN.
D. Verify that the VLAN virtual interface has been correctly created and enabled.
Answer: D
Question 17
Under what circumstances should an administrator prefer local VLANs over end-to-end VLANs?
A. Eighty percent of traffic on the network is destined for Internet sites.
B. There are common sets of traffic filtering requirements for workgroups located in multiple buildings.
C. Eighty percent of a workgroup’s traffic is to the workgroup’s own local server.
D. Users are grouped into VLANs independent of physical location.
Answer: A
Explanation
End-to-end VLAN follows the 80/20 rule in which 80 percent of user traffic stays within the local workgroup, whereas 20 percent is destined for a remote resource in the campus network (like Internet…).
In contrast to end-to-end-VLAN, local VLAN follows the 20/80 rule: only 20 percent of traffic is local, whereas 80 percent is destined to a remote re-source across the core layer -> A is correct.
Question 18
Which of the following statements is true about the 80/20 rule (Choose two)?
A. 20 percent of the traffic on a network segment should be local.
B. no more than 20 percent of the network traffic should be able to move across a backbone.
C. no more than 80 percent of the network traffic should be able to move across a backbone.
D. 80 percent of the traffic on a network segment should be local.
Answer: B D
Explanation
The 80/20 rule states that 80 percent of user traffic stays within the local workgroup, whereas 20 percent is destined for a remote resource in the campus network
Question 19
Which two statements are true about best practices in VLAN design? (Choose two.)
A. Routing should occur at the access layer if voice VLANs are utilized. Otherwise, routing should occur at the distribution layer.
B. Routing may be performed at all layers but is most commonly done at the core and distribution layers.
C. Routing should not be performed between VLANs located on separate switches.
D. VLANs should be local to a switch.
E. VLANs should be localized to a single switch unless voice VLANs are being utilized.
Answer: B D
Explanation
First let’s review main characteristics of three layers in a campus network:
* Access layer:
+ Low cost per switch port
+ High port density
+ Scalable uplinks to higher layers
+ User access functions such as VLAN membership, traffic and protocol filtering, and quality of service (QoS)
+ Resiliency through multiple uplinks
* Distribution Layer:
+ Aggregation of multiple access-layer devices
+ High Layer 3 throughput for packet handling
+ Security and policy-based connectivity functions through access lists or packet filters
+ QoS features
+ Scalable and resilient high-speed links to the core and access layers
* Core layer:
+ Very high throughput at Layer 3
+ No costly or unnecessary packet manipulations (access lists, packet filtering)
+ Redundancy and resilience for high availability
+ Advanced QoS functions
We can see at Distribution and Core layers, Layer 3 throughput (routing) is very high -> B is correct.
Nowadays, end-to-end VLANs are not recommended in an enterprise network, unless there is a good reason. In an end-to-end VLAN, broadcast traffic is carried over from one end of the network to the other, creating the possibility for a broadcast storm or Layer 2 bridging
loop to spread across the whole extent of a VLAN. This can exhaust the bandwidth of distribution and core-layer links, as well as switch CPU resources. Now the storm or loop has disrupted users on the end-to-end VLAN, in addition to users on other VLANs that might
be crossing the core.
When such a problem occurs, troubleshooting becomes more difficult. In other words, the risks of end-to-end VLANs outweigh the convenience and benefits.
From that we can infer VLAN traffic should be local to the switch -> D is correct.
Question 20

Refer to the exhibit. The user who is connected to interface FastEthernet 0/1 is on VLAN 10 and cannot access network resources. On the basis of the information in the exhibit, which command sequence would correct the problem?
A. SW1(config)# vlan 10
SW1(config-vlan)# no shut
B. SW1(config)# interface fastethernet 0/1
SW1(config-if)# switchport mode access
SW1(config-if)# switchport access vlan 10
C. SW1(config)# interface fastethernet 0/1
SW1(config-if)# switchport mode access
D. SW1(config)# vlan 10
SW1(config-vlan)# state active
E. SW1(config)# interface fastethernet 0/1
SW1(config-if)# no shut
Answer: E
Question 21
Refer to the exhibit. On the basis of the output generated by the show commands, which two statements are true? (Choose two)

A. Interface gigabitethernet 0/1 has been configured as Layer 3 ports.
B. Interface gigabitethernet 0/1 does not appear in the show vlan output because switchport is enabled.
C. Interface gigabitethernet 0/1 does not appear in the show vlan output because it is configured as a trunk interface.
D. VLAN2 has been configured as the native VLAN for the 802.1q trunk on interface gigabitethernet 0/1.
E. Traffic on VLAN 1 that is sent out gigabitethernet 0/1 will have an 802.1q header applied.
F. Traffic on VLAN 2 that is sent out gigabitethernet 0/1 will have an 802.1q header applied.
Answer: C F
Explanation
From the output of show interface gigabitethernet 0/1 switchport command we can see this port is currently configured as trunked port (Operational Mode: trunk) and uses 802.1q encapsulation. So surely the “show vlan” command will not list this port -> C is correct.
Also from the first output we learned the native VLAN is VLAN 1 (Trunking Native Mode VLAN:1) so only traffic from this VLAN is sent untagged -> traffic sent from VLAN 2 out this port will have an 802.1q header applied -> F is correct.
Question 22
When you issue a command show port 3/1 on an Ethernet port, you observe the ‘Giants’ column has a non-zero entry. What could cause of this?
A. IEEE 802.1Q
B. IEEE 802.10
C. Misconfigured NIC
D. User configuration
E. All of the above
Answer: A
Explanation
Generally, frames that are greater than 1522 bytes are categorized as giant frames (notice that a normal Ethernet frame has a size that ranges from 64 bytes to 1518 bytes). Giant frames often are the result of some protocol-tagging mechanisms, for example 802.1Q frames (1522 bytes), MPLS (1518 + 4 * n, where n is the number of stacked labels), ISL frames (1548 bytes).
There are nothing wrong with giant frames, just make sure you configure both end devices to support these frames.
Note: In fact, frames that are created by 802.1Q are often known as baby giants (frames that are slightly larger than 1518 bytes).
Question 23
You want to configure a switched internetwork with multiple VLANs as shown above. Which of the following commands should you issue on SwitchA for the port connected to SwitchB?

B. switchport access vlan 5
C. switchport mode access vlan 5
D. switchport trunk native vlan 5
Answer: A
Explanation
To support interVLAN routing, the links between two switches must be configured as trunk link.
Question 24
Refer to the exhibit. VLAN 1 and VLAN 2 are configured on the trunked links between Switch A and Switch B. Port Fa 0/2 on Switch B is currently in a blocking state for both VLANs. What should be done to load balance VLAN traffic between Switch A and Switch B?

A. Lower the port priority for VLAN 1 on port 0/1 for Switch A.
B. Lower the port priority for VLAN 1 on port 0/2 for Switch A.
C. Make the bridge ID of Switch B lower than the ID of Switch A.
D. Enable HSRP on the access ports.
Answer: B
Explanation
In general, lower the port priority for VLAN 1 will lower the Root Bridge ID for port Fa0/2 on Switch A -> traffic for VLAN 1 will flow via Fa0/2 link.
Question 25
On a multilayer Catalyst switch, which interface command is used to convert a Layer 3 interface to a Layer 2 interface?
A. switchport access vlan vlan-id
B. switchport
C. switchport mode access
D. no switchport
Answer: B
Question 26
Refer to the exhibit and the show interfaces fastethernet0/1 switchport outputs. Users in VLAN 5 on switch SW_A complain that they do not have connectivity to the users in VLAN 5 on switch SW_B. What should be done to fix the problem?

B. Create switch virtual interfaces (SVI) on both switches to route the traffic.
C. Define VLAN 5 in the allowed list for the trunk port on SW_A.
D. Disable pruning for all VLANs in both switches.
E. Define VLAN 5 in the allowed list for the trunk port on SW_B.
Answer: C
Explanation
SW_A is missing VLAN 5 in the “Trunking VLANs Enabled”, that means the trunk link currently does not accept traffic from VLAN 5 to be sent on the link.
Question 27
Refer to the show interface Gi0/1 switchport command output shown in the exhibit. Which two statements are true about this interface? (Choose two)

A. This interface is a member of a voice VLAN.
B. This interface is configured for access mode.
C. This interface is a dot1q trunk passing all configured VLANs.
D. This interface is a member of VLAN 7.
E. This interface is a member of VLAN 1.
Answer: B D
Question 28
In the three-layer hierarchical network design model; what’s associated with the access layer? (Choose two)
A. optimized transport structure
B. high port density
C. boundary definition
D. data encryption
E. local VLANs
F. route summaries
Answer: B E
Explanation
Main characteristics of three layers in the three-layer hierarchical network design model:
* Access layer:
+ Low cost per switch port
+ High port density
+ Scalable uplinks to higher layers
+ User access functions such as VLAN membership, traffic and protocol filtering, and quality of service (QoS)
+ Resiliency through multiple uplinks
* Distribution Layer:
+ Aggregation of multiple access-layer devices
+ High Layer 3 throughput for packet handling
+ Security and policy-based connectivity functions through access lists or packet filters
+ QoS features
+ Scalable and resilient high-speed links to the core and access layers
* Core layer:
+ Very high throughput at Layer 3
+ No costly or unnecessary packet manipulations (access lists, packet filtering)
+ Redundancy and resilience for high availability
+ Advanced QoS functions
Also, end-to-end VLANs and local VLANs belong to access layer.
Question 29
Refer to the following exhibits:
Exhibit #1

Exhibit #2

Study the exhibits carefully. The switchport output in Exhibit #1 displays the default settings of interface FastEthernet 0/13 on switch Sw1. Figure 2 displays the desired interface settings. Which command sequence would configure interface FastEthernet 0/13 as displayed in Exhibit #2?
A.
Sw1(config-if)# switchport trunk encapsulation dot1q
Sw1 (config-if)# switchport mode dynamic auto
Sw1 (config-if)# switchport trunk native DATA
Sw1 (config-if)# switchport trunk allowed vlan add 1,10,20
B.
Sw1(config-if)# switchport trunk encapsulation dot1q
Sw1(config-if)# switchport mode dynamic desirable
Sw1(config-if)# switchport trunk native vlan DATA
Sw1(config-if)# switchport trunk allowed vlan 1,10,20
C.
Sw1 (config-if)# switchport trunk encapsulation dot1q
Sw1 (config-if)# switchport mode trunk
Sw1 (config-if)# switchport trunk native DATA
Sw1 (config-if)# switchport trunk allowed vlan 1,10,20
D.
Sw1(config-if)# switchport trunk encapsulation dot1q
Sw1(config-if)#switchport mode dynamic desirable
Sw1(config-if)#switchport trunk native vlan 10
E.
Sw1 (config-if)# switchport trunk encapsulation dot1q
Sw1 (config-if)# switchport mode dynamic desirable
Sw1 (config-if)# switchport trunk native vlan 10
Sw1 (config-if)# switchport trunk allowed vlan 1,10,20
Answer: E
Question 30
What is the result of these commands?
| Switch (config)#interface range fa0/0-5 Switch(config-if-range)#switchport access vlan 2 |
B. One new vlan is created on five switch ports
C. Six new vlans are created on six switch ports
D. One new vlan is created with the vlan number 2
Answer: D
Explanation
If the administrator has not created VLAN 2 before typing this command, a message will appear informing that VLAN 2 is created automatically.
Question 31
Which three statements apply to access control of both bridged and routed traffic for VLANs? (Choose three)
A. Router ACLs can be applied to the input and output directions of a VLAN interface
B. Bridged ACLs can be applied to the input and output directions of a VLAN interface
C. Only router ACLs can be applied to a VLAN interface
D. VLAN maps can be applied to a VLAN interface
E. VLAN maps and router ACLs can be used in combination
Answer: A C E
Explanation
Bridged ACL (or VLAN Access-list, or VLAN map) is used to filter traffic that is flowing within a VLAN. It can only be applied to a VLAN, not interface -> C is correct.
An Interface VLAN (or Switch Virtual Interface – SVI) is very similar to a physical interface on a router, although it is a virtual interface only. We can apply Router ACL to the inbound and outbound direction of a VLAN interface -> A is correct.
To apply access control to both bridged and routed traffic, you can use VACLs alone or a combination of VACLs and ACLs. You can define ACLs on the VLAN interfaces to apply access control to both the ingress and egress routed traffic. You can define a VACL to apply access control to the bridged traffic. -> E is correct.
Note: In CCNA we learned about Access list, in fact it is Router Access list.
Question 32
When you create a network implementation for a VLAN solution, what is one procedure that you should include in your plan?
A. Perform an incremental implementation of components.
B. Implement the entire solution and then test end-to-end to make sure that it is performing as designed.
C. Implement trunking of all VLANs to ensure that traffic is crossing the network as needed before performing any pruning of VLANs.
D. Test the solution on the production network in off hours.
Answer: A
Question 33
Two switches SA and SB are connected as shown below. Given the below partial configuration, which two statements are true about VLAN traffic? (Choose two)

B – VLANs 6-10 have a port priority of 128 on fa0/10.
C – VLANs 6-10 will use fa0/10 as a backup only.
D – VLANs 1-10 are configured to load share between fa0/10 and fa0/12.
Answer: C D
Explanation:
Let’s assume that SA is the root bridge for all VLANs, it will make the explanation a bit clearer…
First we should understand what will happen if nothing is configured (use default values). Because we assumed that SA is the root bridge so all of its ports will forward. SB will need to block one of its ports to avoid a bridging loop between the two switches. But how does SB select its blocked port? Well, the answer is based on the BPDUs it receives from SA. A BPDU is superior than another if it has:
1. A lower Root Bridge ID
2. A lower path cost to the Root
3. A lower Sending Bridge ID
4. A lower Sending Port ID
These four parameters are examined in order. In this specific case, all the BPDUs sent by SA have the same Root Bridge ID, the same path cost to the Root and the same Sending Bridge ID. The only parameter left to select the best one is the Sending Port ID (Port ID = port priority + port index). If using default values, the default port priority’s value is 32 or 128 (128 is much more popular today but 32 is also a default port priority’s value), so SB will compare port index values, which are unique to each port on the switch, and because Fa0/12 is inferior to Fa0/10, SB will select the port connected with Fa0/10 (of SA) as its root port and block the other port.

To change the default decision of selecting root port, we can change the port priority of each interface. The above picture is true for VLAN 1-5 because port Fa0/10 has a lower port-priority so the peer port will be chosen as the root port. For VLAN 6-10, port Fa0/12 has higher priority ID (lower port priority value) so SB will block its upper port.
For answer A – “VLANs 1-5 will be blocked if fa0/10 goes down” – is not correct because if Fa0/10 goes down, SB will unblock its lower port therefore VLANs 1-5 will still operate.
For answer B – “VLANs 6-10 have a port priority of 128 on fa0/10″ – is not always correct because VLAN 6-10 can have a different port priority (of 32) according to the Cisco’s link below.
Answer C is correct because VLAN 6-10 uses Fa0/12 link as it main path. Fa0/10 is the backup path and is only opened when port Fa0/12 fails.Answer D is correct because this configuration provide load-balance traffic based on VLAN basis. VLANs 1-5 use Fa0/10 and VLANs 6-10 use Fa0/12 as their main paths.
Note: We can not assure the answer B is always correct so we should choose C and D if the question asks us to give only 2 choices).
