Question 1:
Place the DTP mode with its correct description:
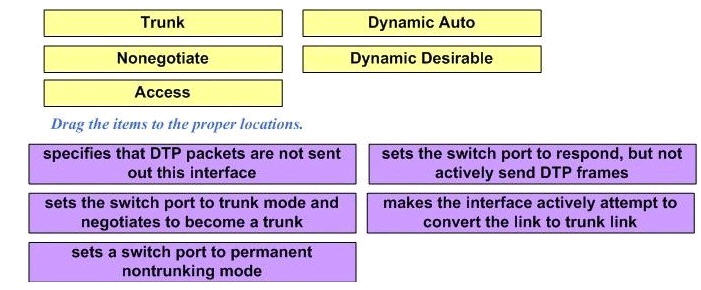
Answer:
1) Trunk: Set the switch port to trunk mode and negotiate to become a trunk.
2) Nonegotiate: Specify that the DTP packets are not sent out of this interface.
3) Access: Set a switch port to permanent nontrunking mode.
4) Dynamic Auto: Set the switch port to respond, but not actively send DTP frames.
5) Dynamic Desirable: Make the interface actively attempt to convert the link to a trunk link. (This means the interface is ready to autonegotiate trunking encapsulation and form a trunk link (using DTP) with a neighbor port in desirable, auto, or on mode.)
Explanation:
Dynamic Trunking Protocol (DTP) is the Cisco-proprietary that actively attempts to negotiate a trunk link between two switches. Below is the switchport modes (or DTP modes) for easy reference:
Question 2:
This is a drag and drop question which is about the correct sequence of steps that a wireless client takes during the process of association with an access point (AP). Drag the items to the proper locations.
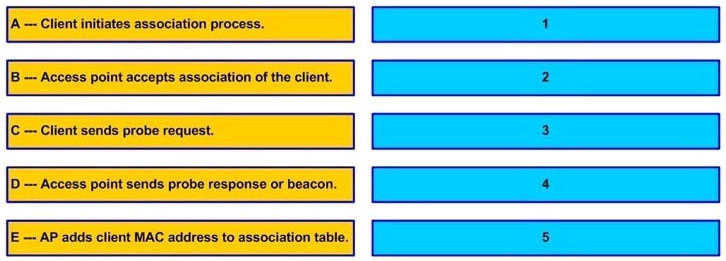 Answer:
Answer:
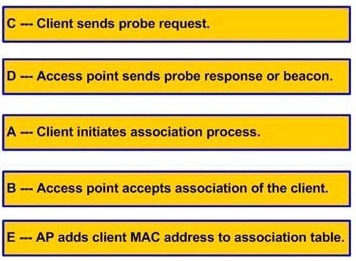
Explanation:
Any wireless client attempting to use the wireless network must first arrange a membership with the AP. Membership with the AP is called an association. The client must send an association request message, and the AP grants or denies the request by sending an association reply message. Once associated, all communications to and from the client must pass through the AP. Clients associate with access points as follows:
1) The client sends a probe request.
2) The AP sends a probe response.
3) The client initiates an association to an AP. Authentication and any other security information is sent to the AP.
4) The AP accepts the association.
5) The AP adds the client’s MAC address to its association table.
Question 3:
Drag and drop question. Drag the items to the proper locations.
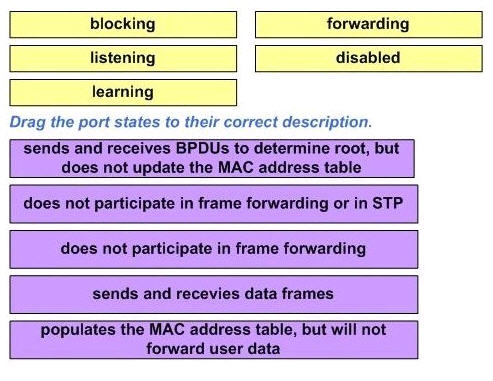 Answer:
Answer:
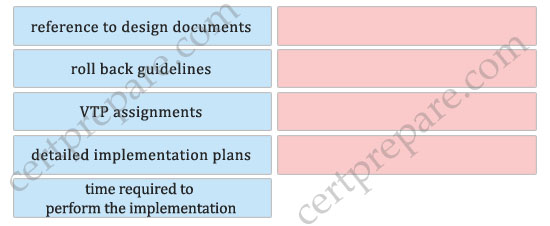
Drag the choices on the left to the boxes on the right that should be included when creating a VLAN-based implementation plan. Not all choices will be used.
 Answer:
Answer:
+ reference to design documents
+ roll back guidelines
+ detailed implementation plans
+ time required to perform the implementation
(In this question we don’t need to sort in the correct order)
Explanation
An implementation plan requires:
+ A description of the task
+ References to design documents
+ Detailed implementation guidelines
+ Detailed rollback guidelines in case of failure
+ The estimated time required for implementation
Question 5
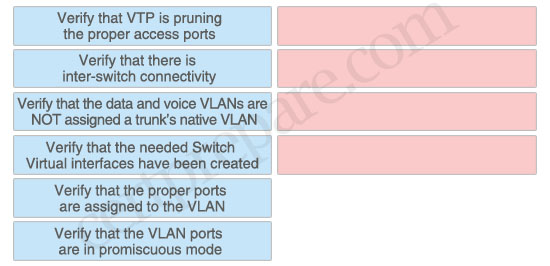
You have a VLAN implementation that requires inter-vlan routing using layer 3 switches. Drag the steps on the left that should be part of the verification plan to the spaces on the right. Not all choices will be used.
Answer:
+ Verify that there is inter-switch connectivity
+ Verify that the data and voice VLANs are NOT assigned a trunk’s native VLAN
+ Verify that the needed Switch Virtual interfaces have been created
+ Verify that the proper ports are assigned to the VLAN
Explanation
“The data and voice VLANs are NOT assigned a trunk’s native VLAN”: Voice VLAN configuration is only supported on switch access ports; voice VLAN configuration is not supported on trunk ports.
Question 6
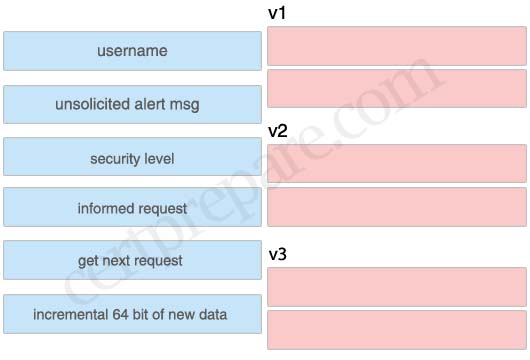
Match the SNMP versions and associated features
Answer:
v1:
+ get next request
+ unsolicited alert msg
v2:
+ informed request
+ incremental 64 bit of new data
v4:
+ user name
+ security level
Question 7
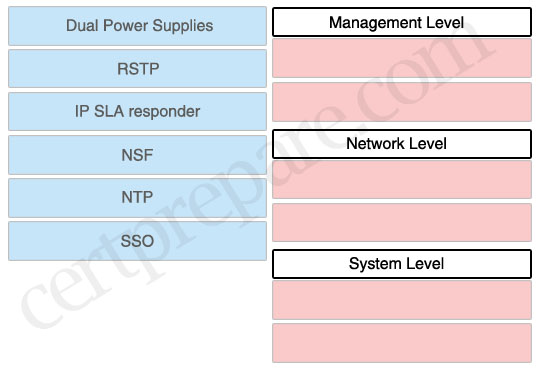
Categorize the high availability network resource or feature with the management level, network level, or system level used.
 Answer:
Answer:
Management Level:
+ IP SLA responder
+ NTP
Network Level:
+ RSTP
+ NSF
System Level:
+ Dual Power Supplies
+ SSO
Question 8
Match the HSRP states on the left with the correct definition on the right.

Answer:
+ Initial: State from which the router begin the HSRP process
+ Standby: A candidate to become the next active router
+ Learn: The router is still waiting to hear from the active router
+ Active: The router is currently forwarding packets
+ Listen: Listens for hello messages from the active and standby router
+ Speak: Participates in the election for the active or standby router
Question 9
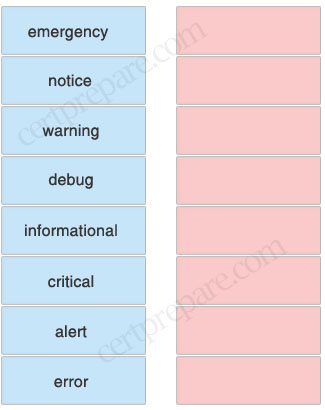
Syslog information can generate messages up to and including the configured severity level. Organize the levels by dragging each name from the left to the right. Put the highest level at the top and lowest at the bottom.
 Answer:
Answer:
1) emergency
2) alert
3) critical
4) error
5) warning
6) notice
7) informational
8) debug
Explanation
The syslog levels and descriptions are listed below:
Question 10
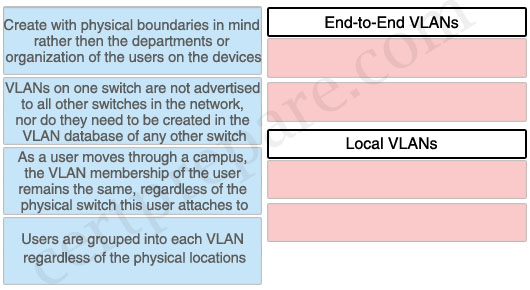
Match the Attributes on the left with the types of VLAN designs on right.
Answer:
End-to-End VLANs:
+ As a user moves through a campus, the VLAN membership of the user remains the same, regardless of the physical switch this user attaches to.
+ Users are grouped into each VLAN regardless of the physical locations.
Local VLANs:
+ Create with Physical boundaries in mind rather then the departments or organization of the users on the devices.
+ VLANs on one switch are not advertised to all other switches in the network, nor do they need to be created in the VLAN database of any other switch.
Question 11
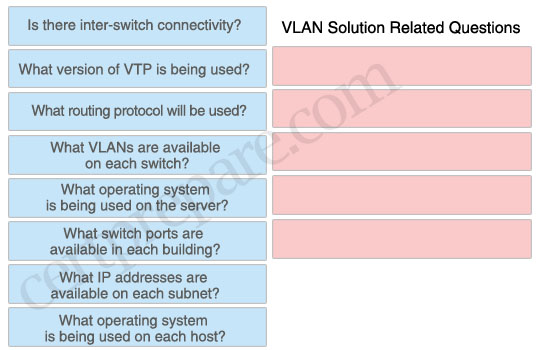
You have been tasked with planning a VLAN solution that will connect a seiver in one buliding to several hosts in another building. The solution should be built using the local vlan model and layer 3 switching at the distribution layer. Identify the questions related to this vlan solution that would ask the network administrator before you start the planning by dragging them into the target zone one the right. Not all questions will be used.
 Answer:
Answer:
+ Is there inter-switch connectivity?
+ What routing protocol will be used?
+ What VLANs are available on each switch?
+ What switch ports are available in each building?
+ What IP addresses are available on each subnet?
Question 12
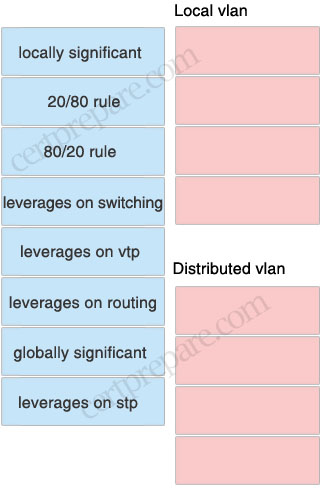 Answer:
Answer:
Local vlan:
+ 20/80 rule
+ leverages on stp
+ leverages on routing
+ locally significant
Distributed vlan:
+ 80/20 rule
+ leverages on vtp
+ leverages on switching
+ globally significant
the data and voice VLANs are NOT assigned a trunk’s native VLAN
Question 13
Prioritize the traffic types by dragging them from the left to the appropriate Cisco priority level on the right. Put the highest priority at the top and lowest priority at the bottom.
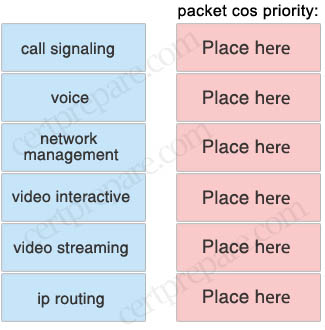 Answer:
Answer:
+ voice
+ video interactive
+ video streaming
+ call signaling
+ ip routing
+ network management
Question 14
Drag and drop the appropriate characteristics of Local VLANs and End-to-end VLANs
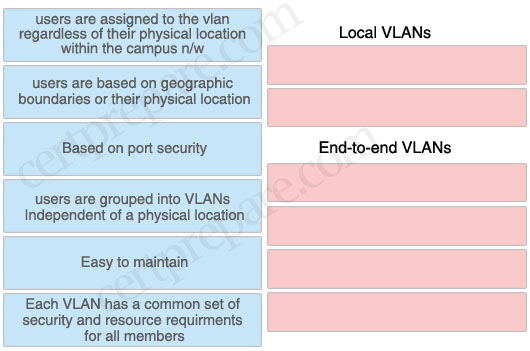
Answer:
Local VLANs:
+ easy to maintain
+ users are based on geographic boundaries or their physical location
End-to-end VLANs:
+ users are grouped into VLANs independent of a physical location
+ each VLAN has a common set of security and resource
+ users are assigned to the vlan regardless of their physical location within the campus n/w
+ Based on port security
Explanation
End-to-end VLAN: VLAN members reside on different switches throughout the network. They are used when hosts are assigned to VLANs for policy reasons, rather than physical location.
Local VLAN: Hosts are assigned to VLANs based on their location, such as a floor in a building. This design is more scalable and easier to troubleshoot because the traffic flow is more deterministic. It enables more redundancy and minimizes failure domains.
(Reference: CCNP SWITCH 642-813 Quick Reference Guide)
Question 15
Drag the steps on the left that should be part of a VLAN-based verification plan to the spaces on the right. Not all choices will be used.
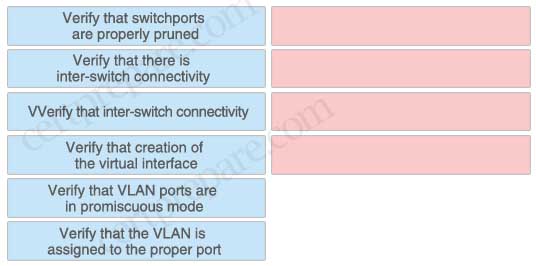
Answer:
+ Verify that there is inter-switch connectivity
+ Verify that switchports are properly pruned
+ Verify that creation of the virtual interface
+ Verify that the VLAN is assigned to the proper port
Question 16
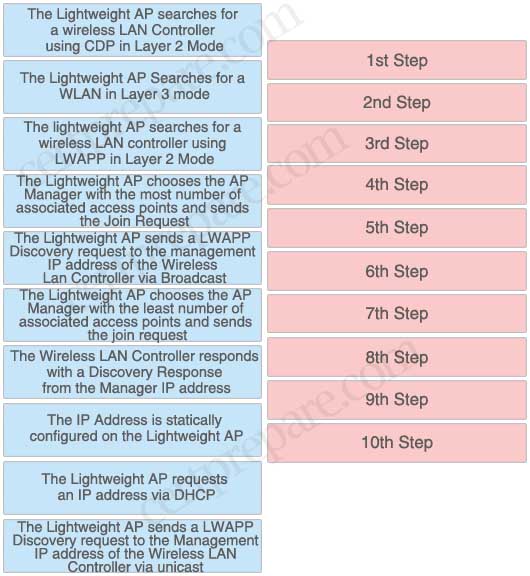
Wireless LWAPP Association and Discovery Process Drag & Drop. Note not all options are used
 Answer:
Answer:
+ The IP Address is statically configured on the Lightweight AP
+ The Lightweight AP requests an IP address via DHCP
+ The Lightweight AP searches for a wireless LAN controller using LWAPP in Layer 2 Mode
+ The Lightweight AP sends a LWAPP Discovery request to the management IP address of the Wireless LAN Controller via Broadcast
+ The Wireless LAN Controller responds with a Discovery Response from the Manager IP address
+ The Lightweight AP chooses the AP Manager with the least number of associated access points and sends the join request
Explanation
This sequence of events must occur in order for an LAP to register to a WLC:
1. The LAPs issue a DHCP discovery request to get an IP address, unless it has previously had a static IP address configured.
2. The LAP sends LWAPP discovery request messages to the WLCs.
3. Any WLC that receives the LWAPP discovery request responds with an LWAPP discovery response message.
4. From the LWAPP discovery responses that the LAP receives, the LAP selects a WLC to join.
5. The LAP then sends an LWAPP join request to the WLC and expects an LWAPP join response.
6. The WLC validates the LAP and then sends an LWAPP join response to the LAP.
7. The LAP validates the WLC, which completes the discovery and join process. The LWAPP join process includes mutual authentication and encryption key derivation, which is used to secure the join process and future LWAPP control messages.
8. The LAP registers with the controller.
Place the DTP mode with its correct description:

1) Trunk: Set the switch port to trunk mode and negotiate to become a trunk.
2) Nonegotiate: Specify that the DTP packets are not sent out of this interface.
3) Access: Set a switch port to permanent nontrunking mode.
4) Dynamic Auto: Set the switch port to respond, but not actively send DTP frames.
5) Dynamic Desirable: Make the interface actively attempt to convert the link to a trunk link. (This means the interface is ready to autonegotiate trunking encapsulation and form a trunk link (using DTP) with a neighbor port in desirable, auto, or on mode.)
Explanation:
Dynamic Trunking Protocol (DTP) is the Cisco-proprietary that actively attempts to negotiate a trunk link between two switches. Below is the switchport modes (or DTP modes) for easy reference:
| Mode | Function |
| Dynamic Auto | Creates the trunk based on the DTP request from the neighboring switch. |
| Dynamic Desirable | Communicates to the neighboring switch via DTP that the interface would like to become a trunk if the neighboring switch interface is able to become a trunk. |
| Trunk | Automatically enables trunking regardless of the state of the neighboring switch and regardless of any DTP requests sent from the neighboring switch. |
| Access | Trunking is not allowed on this port regardless of the state of the neighboring switch interface and regardless of any DTP requests sent from the neighboring switch. |
| Nonegotiate | Prevents the interface from generating DTP frames. This command can be used only when the interface switchport mode is access or trunk. You must manually configure the neighboring interface as a trunk interface to establish a trunk link. |
Question 2:
This is a drag and drop question which is about the correct sequence of steps that a wireless client takes during the process of association with an access point (AP). Drag the items to the proper locations.


Any wireless client attempting to use the wireless network must first arrange a membership with the AP. Membership with the AP is called an association. The client must send an association request message, and the AP grants or denies the request by sending an association reply message. Once associated, all communications to and from the client must pass through the AP. Clients associate with access points as follows:
1) The client sends a probe request.
2) The AP sends a probe response.
3) The client initiates an association to an AP. Authentication and any other security information is sent to the AP.
4) The AP accepts the association.
5) The AP adds the client’s MAC address to its association table.
Question 3:
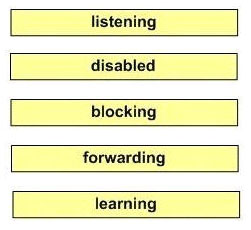
Drag and drop question. Drag the items to the proper locations.


1) Listening: sends and receives BPDUs to determine root, but does not update the MAC address table.
2) Disabled: does not participate in frame forwarding or in STP.
3) Blocking: does not participate in frame forwarding.
4) Fowarding: sends and receives data frames.
5) Learning: populates the MAC address table, but will not forward user data.
2) Disabled: does not participate in frame forwarding or in STP.
3) Blocking: does not participate in frame forwarding.
4) Fowarding: sends and receives data frames.
5) Learning: populates the MAC address table, but will not forward user data.
Notice: A port begins its life in a Disabled state, moving through several passive states and, finally, into an active state if allowed to forward traffic.
Question 4Drag the choices on the left to the boxes on the right that should be included when creating a VLAN-based implementation plan. Not all choices will be used.

+ reference to design documents
+ roll back guidelines
+ detailed implementation plans
+ time required to perform the implementation
(In this question we don’t need to sort in the correct order)
Explanation
An implementation plan requires:
+ A description of the task
+ References to design documents
+ Detailed implementation guidelines
+ Detailed rollback guidelines in case of failure
+ The estimated time required for implementation
Question 5
You have a VLAN implementation that requires inter-vlan routing using layer 3 switches. Drag the steps on the left that should be part of the verification plan to the spaces on the right. Not all choices will be used.

+ Verify that there is inter-switch connectivity
+ Verify that the data and voice VLANs are NOT assigned a trunk’s native VLAN
+ Verify that the needed Switch Virtual interfaces have been created
+ Verify that the proper ports are assigned to the VLAN
Explanation
“The data and voice VLANs are NOT assigned a trunk’s native VLAN”: Voice VLAN configuration is only supported on switch access ports; voice VLAN configuration is not supported on trunk ports.
Question 6
Match the SNMP versions and associated features

v1:
+ get next request
+ unsolicited alert msg
v2:
+ informed request
+ incremental 64 bit of new data
v4:
+ user name
+ security level
Question 7
Categorize the high availability network resource or feature with the management level, network level, or system level used.

Management Level:
+ IP SLA responder
+ NTP
Network Level:
+ RSTP
+ NSF
System Level:
+ Dual Power Supplies
+ SSO
Question 8
Match the HSRP states on the left with the correct definition on the right.

Answer:
+ Initial: State from which the router begin the HSRP process
+ Standby: A candidate to become the next active router
+ Learn: The router is still waiting to hear from the active router
+ Active: The router is currently forwarding packets
+ Listen: Listens for hello messages from the active and standby router
+ Speak: Participates in the election for the active or standby router
Question 9
Syslog information can generate messages up to and including the configured severity level. Organize the levels by dragging each name from the left to the right. Put the highest level at the top and lowest at the bottom.

1) emergency
2) alert
3) critical
4) error
5) warning
6) notice
7) informational
8) debug
Explanation
The syslog levels and descriptions are listed below:
| Code | Severity | Description |
| 0 | Emergency | system is unusable (such as an imminent system crash) |
| 1 | Alert | action must be taken immediately (such as a corrupted system database) |
| 2 | Critical | Critical conditions (such as a hardware error) |
| 3 | Error | Error conditions |
| 4 | Warning | Warning conditions |
| 5 | Notice | normal but significant condition. It is not an error, but possibly should be handled in a special way |
| 6 | Informational | Informational message |
| 7 | Debug | Debug-level message |
Question 10
Match the Attributes on the left with the types of VLAN designs on right.

End-to-End VLANs:
+ As a user moves through a campus, the VLAN membership of the user remains the same, regardless of the physical switch this user attaches to.
+ Users are grouped into each VLAN regardless of the physical locations.
Local VLANs:
+ Create with Physical boundaries in mind rather then the departments or organization of the users on the devices.
+ VLANs on one switch are not advertised to all other switches in the network, nor do they need to be created in the VLAN database of any other switch.
Question 11
You have been tasked with planning a VLAN solution that will connect a seiver in one buliding to several hosts in another building. The solution should be built using the local vlan model and layer 3 switching at the distribution layer. Identify the questions related to this vlan solution that would ask the network administrator before you start the planning by dragging them into the target zone one the right. Not all questions will be used.

+ Is there inter-switch connectivity?
+ What routing protocol will be used?
+ What VLANs are available on each switch?
+ What switch ports are available in each building?
+ What IP addresses are available on each subnet?
Question 12

Local vlan:
+ 20/80 rule
+ leverages on stp
+ leverages on routing
+ locally significant
Distributed vlan:
+ 80/20 rule
+ leverages on vtp
+ leverages on switching
+ globally significant
the data and voice VLANs are NOT assigned a trunk’s native VLAN
Question 13
Prioritize the traffic types by dragging them from the left to the appropriate Cisco priority level on the right. Put the highest priority at the top and lowest priority at the bottom.

+ voice
+ video interactive
+ video streaming
+ call signaling
+ ip routing
+ network management
Question 14
Drag and drop the appropriate characteristics of Local VLANs and End-to-end VLANs

Local VLANs:
+ easy to maintain
+ users are based on geographic boundaries or their physical location
End-to-end VLANs:
+ users are grouped into VLANs independent of a physical location
+ each VLAN has a common set of security and resource
+ users are assigned to the vlan regardless of their physical location within the campus n/w
+ Based on port security
Explanation
End-to-end VLAN: VLAN members reside on different switches throughout the network. They are used when hosts are assigned to VLANs for policy reasons, rather than physical location.
Local VLAN: Hosts are assigned to VLANs based on their location, such as a floor in a building. This design is more scalable and easier to troubleshoot because the traffic flow is more deterministic. It enables more redundancy and minimizes failure domains.
(Reference: CCNP SWITCH 642-813 Quick Reference Guide)
Question 15
Drag the steps on the left that should be part of a VLAN-based verification plan to the spaces on the right. Not all choices will be used.

Answer:
+ Verify that there is inter-switch connectivity
+ Verify that switchports are properly pruned
+ Verify that creation of the virtual interface
+ Verify that the VLAN is assigned to the proper port
Question 16
Wireless LWAPP Association and Discovery Process Drag & Drop. Note not all options are used

+ The IP Address is statically configured on the Lightweight AP
+ The Lightweight AP requests an IP address via DHCP
+ The Lightweight AP searches for a wireless LAN controller using LWAPP in Layer 2 Mode
+ The Lightweight AP sends a LWAPP Discovery request to the management IP address of the Wireless LAN Controller via Broadcast
+ The Wireless LAN Controller responds with a Discovery Response from the Manager IP address
+ The Lightweight AP chooses the AP Manager with the least number of associated access points and sends the join request
Explanation
This sequence of events must occur in order for an LAP to register to a WLC:
1. The LAPs issue a DHCP discovery request to get an IP address, unless it has previously had a static IP address configured.
2. The LAP sends LWAPP discovery request messages to the WLCs.
3. Any WLC that receives the LWAPP discovery request responds with an LWAPP discovery response message.
4. From the LWAPP discovery responses that the LAP receives, the LAP selects a WLC to join.
5. The LAP then sends an LWAPP join request to the WLC and expects an LWAPP join response.
6. The WLC validates the LAP and then sends an LWAPP join response to the LAP.
7. The LAP validates the WLC, which completes the discovery and join process. The LWAPP join process includes mutual authentication and encryption key derivation, which is used to secure the join process and future LWAPP control messages.
8. The LAP registers with the controller.
