Em mới tìm hiểu về PIX chưa biết nhiều, mong các anh chị giúp đỡ .
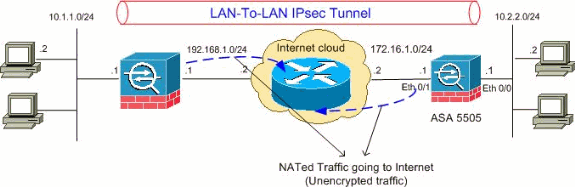
em có topo như sau:

với topo trên, em đã cấu hình địa chỉ và định tuyến đầy đủ cho các router R1, R2, Internet.
em dùng thêm 2 router để làm 2 PC
Em thử dùng lệnh : Telnet từ PC1 tới PC2 nhưng không thành công.
mặc định, PIx không cho gói tin ICMP đi qua, có phải ta không thể dùng lệnh ping để kiểm tra xem đường hầm VPN giữa 2 PC đã up hay chưa ? Nếu như vậy em phải làm thế nào để kiểm tra kết nối VPN có thành công hay không ?
Em phải làm thế nào để khi dùng lệnh : show crypto ipsec sa --> để có thống số là bao nhiêu gói tin được mã hóa, bao nhiều gói tin được giải mã như sau :
Em đang rất gấp để hoàn thiện bài tập này. Mong các anh xem giúp phần cấu hình của em có bị sai gì không?
Em xin cám ơn trước !
Đây là file cấu hình của 2 FW
FW1 (PIX1):
FW2 (PIX2):
em có topo như sau:

với topo trên, em đã cấu hình địa chỉ và định tuyến đầy đủ cho các router R1, R2, Internet.
em dùng thêm 2 router để làm 2 PC
Em thử dùng lệnh : Telnet từ PC1 tới PC2 nhưng không thành công.
mặc định, PIx không cho gói tin ICMP đi qua, có phải ta không thể dùng lệnh ping để kiểm tra xem đường hầm VPN giữa 2 PC đã up hay chưa ? Nếu như vậy em phải làm thế nào để kiểm tra kết nối VPN có thành công hay không ?
Em phải làm thế nào để khi dùng lệnh : show crypto ipsec sa --> để có thống số là bao nhiêu gói tin được mã hóa, bao nhiều gói tin được giải mã như sau :
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
Em xin cám ơn trước !
Đây là file cấu hình của 2 FW
FW1 (PIX1):
PIX1# show running-config
: Saved
:
PIX Version 8.0(2)
!
hostname PIX1
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 20.0.0.2 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.1.1.1 255.255.255.0
!
interface Ethernet2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet4
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list toInside extended permit icmp any host 20.0.0.3
access-list toPIX2 extended permit ip 10.1.1.0 255.255.255.0 10.2.2.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 20.0.0.4-20.0.0.6
nat (inside) 0 access-list toPIX2
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 20.0.0.3 10.1.1.10 netmask 255.255.255.255
access-group toInside in interface outside
route outside 0.0.0.0 0.0.0.0 20.0.0.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set mytransformset esp-3des esp-sha-hmac
crypto map mymap 2 match address toPIX2
crypto map mymap 2 set peer 50.0.0.2
crypto map mymap 2 set transform-set mytransformset
crypto map mymap interface outside
crypto isakmp enable outside
crypto isakmp policy 2
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
tunnel-group 50.0.0.2 type ipsec-l2l
tunnel-group 50.0.0.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:1ce56970d844ef4eae7379f22a3857d2
: end
PIX1#
: Saved
:
PIX Version 8.0(2)
!
hostname PIX1
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 20.0.0.2 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.1.1.1 255.255.255.0
!
interface Ethernet2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet4
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list toInside extended permit icmp any host 20.0.0.3
access-list toPIX2 extended permit ip 10.1.1.0 255.255.255.0 10.2.2.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 20.0.0.4-20.0.0.6
nat (inside) 0 access-list toPIX2
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 20.0.0.3 10.1.1.10 netmask 255.255.255.255
access-group toInside in interface outside
route outside 0.0.0.0 0.0.0.0 20.0.0.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set mytransformset esp-3des esp-sha-hmac
crypto map mymap 2 match address toPIX2
crypto map mymap 2 set peer 50.0.0.2
crypto map mymap 2 set transform-set mytransformset
crypto map mymap interface outside
crypto isakmp enable outside
crypto isakmp policy 2
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
tunnel-group 50.0.0.2 type ipsec-l2l
tunnel-group 50.0.0.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:1ce56970d844ef4eae7379f22a3857d2
: end
PIX1#
PIX2# show running-config
: Saved
:
PIX Version 8.0(2)
!
hostname PIX2
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 50.0.0.2 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.2.2.1 255.255.255.0
!
interface Ethernet2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet4
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list toInside extended permit icmp any host 50.0.0.3
access-list toPIX1 extended permit ip 10.2.2.0 255.255.255.0 10.1.1.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 50.0.0.4-50.0.0.6
nat (inside) 0 access-list toPIX1
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 50.0.0.3 10.2.2.10 netmask 255.255.255.255
access-group toInside in interface outside
route outside 0.0.0.0 0.0.0.0 50.0.0.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set mytransformset esp-3des esp-sha-hmac
crypto map mymap 2 match address toPIX1
crypto map mymap 2 set peer 20.0.0.2
crypto map mymap 2 set transform-set mytransformset
crypto map mymap interface outside
crypto isakmp enable outside
crypto isakmp policy 2
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
tunnel-group 20.0.0.2 type ipsec-l2l
tunnel-group 20.0.0.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:fe8afb4e37da97e75d172e7fcefc3ec8
: end
PIX2#
: Saved
:
PIX Version 8.0(2)
!
hostname PIX2
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 50.0.0.2 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.2.2.1 255.255.255.0
!
interface Ethernet2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet4
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list toInside extended permit icmp any host 50.0.0.3
access-list toPIX1 extended permit ip 10.2.2.0 255.255.255.0 10.1.1.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 50.0.0.4-50.0.0.6
nat (inside) 0 access-list toPIX1
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 50.0.0.3 10.2.2.10 netmask 255.255.255.255
access-group toInside in interface outside
route outside 0.0.0.0 0.0.0.0 50.0.0.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set mytransformset esp-3des esp-sha-hmac
crypto map mymap 2 match address toPIX1
crypto map mymap 2 set peer 20.0.0.2
crypto map mymap 2 set transform-set mytransformset
crypto map mymap interface outside
crypto isakmp enable outside
crypto isakmp policy 2
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
tunnel-group 20.0.0.2 type ipsec-l2l
tunnel-group 20.0.0.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:fe8afb4e37da97e75d172e7fcefc3ec8
: end
PIX2#
Comment