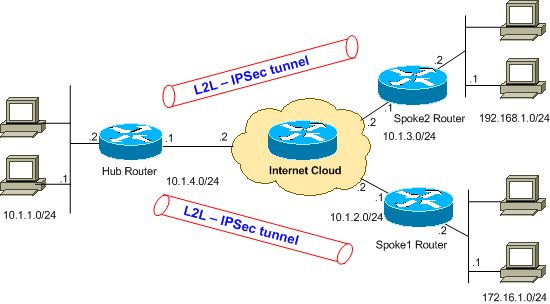
em có mô hình như hình trên
https://lh3.googleusercontent.com/zE...E=w711-h420-no
thông tin cấu hình router saigon
!
version 12.4
service timestamps log datetime msec
service timestamps debug datetime msec
no service password-encryption
!
hostname HCM-R
!
!
!
enable secret 5 $1$8Fwe$I.fE7fBzTMhqf6sr/Jx8g/
!
!
!
ip dhcp pool vlan10
network 192.168.1.0 255.255.255.192
default-router 192.168.1.62
ip dhcp pool vlan20
network 192.168.1.64 255.255.255.192
default-router 192.168.1.126
ip dhcp pool vlan30
network 192.168.1.128 255.255.255.224
default-router 192.168.1.158
ip dhcp pool vlan40
network 192.168.1.160 255.255.255.224
default-router 192.168.1.190
ip dhcp pool vlan50
network 192.168.1.192 255.255.255.240
default-router 192.168.1.206
!
ip cef
no ipv6 cef
!
!
!
username admin secret 5 $1$NZyN$NL5zMBfHeZXWu09g8za7Z.
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp key saigonhanoi address 200.0.0.6
crypto isakmp key saigonnhamay address 200.0.0.10
!
!
crypto ipsec security-association lifetime seconds 1800
!
crypto ipsec transform-set vpnset esp-des esp-md5-hmac
!
crypto map vpnmap 10 ipsec-isakmp
set peer 200.0.0.6
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
crypto map vpnmap 20 ipsec-isakmp
set peer 200.0.0.10
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/0.10
encapsulation dot1Q 10
ip address 192.168.1.62 255.255.255.192
!
interface FastEthernet0/0.20
encapsulation dot1Q 20
ip address 192.168.1.126 255.255.255.192
!
interface FastEthernet0/0.30
encapsulation dot1Q 30
ip address 192.168.1.158 255.255.255.224
!
interface FastEthernet0/0.40
encapsulation dot1Q 40
ip address 192.168.1.190 255.255.255.224
!
interface FastEthernet0/0.50
encapsulation dot1Q 50
ip address 192.168.1.206 255.255.255.240
!
interface FastEthernet0/1
description "ket noi toi ISP"
ip address 200.0.0.2 255.255.255.252
duplex auto
speed auto
crypto map vpnmap
!
interface Vlan1
no ip address
!
ip classless
ip route 0.0.0.0 0.0.0.0 200.0.0.1
!
ip flow-export version 9
!
!
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.4.0 0.0.0.255
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login local
!
!
!
end
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++
thông tin cấu hình trên router hanoi
!
version 12.4
service timestamps log datetime msec
service timestamps debug datetime msec
service password-encryption
!
hostname HANOI
!
!
!
enable secret 5 $1$dqE5$uY4NBhtPEiLdHECR2IrDv.
!
!
!
ip dhcp pool vlan10
network 192.168.2.0 255.255.255.192
default-router 192.168.2.62
dns-server 192.168.2.161
ip dhcp pool vlan20
network 192.168.2.64 255.255.255.192
default-router 192.168.2.126
dns-server 192.168.2.161
ip dhcp pool vlan30
network 192.168.2.128 255.255.255.224
default-router 192.168.2.158
dns-server 192.168.2.161
ip dhcp pool vlan40
network 192.168.2.160 255.255.255.224
default-router 192.168.2.190
dns-server 192.168.2.161
ip dhcp pool vlan50
network 192.168.2.192 255.255.255.240
default-router 192.168.2.206
dns-server 192.168.2.161
!
ip cef
no ipv6 cef
!
!
!
username admin secret 5 $1$Blqb$NPsUIq4PINtKjeJR8AraO0
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp key saigonhanoi address 200.0.0.2
!
!
crypto ipsec security-association lifetime seconds 1800
!
crypto ipsec transform-set vpnset esp-des esp-md5-hmac
!
crypto map vpnmap 10 ipsec-isakmp
set peer 200.0.0.2
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
description "ket noi toi ISP"
ip address 200.0.0.6 255.255.255.252
duplex auto
speed auto
crypto map vpnmap
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.10
encapsulation dot1Q 10
ip address 192.168.2.62 255.255.255.192
!
interface FastEthernet0/1.20
encapsulation dot1Q 20
ip address 192.168.2.126 255.255.255.192
!
interface FastEthernet0/1.30
encapsulation dot1Q 30
ip address 192.168.2.158 255.255.255.224
!
interface FastEthernet0/1.40
encapsulation dot1Q 40
ip address 192.168.2.190 255.255.255.224
!
interface FastEthernet0/1.50
encapsulation dot1Q 50
ip address 192.168.2.206 255.255.255.240
!
interface Vlan1
no ip address
!
ip classless
ip route 0.0.0.0 0.0.0.0 200.0.0.9
ip route 0.0.0.0 0.0.0.0 200.0.0.5
!
ip flow-export version 9
!
!
access-list 100 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login local
!
!
!
end
+++++++++++++++++++++++++++++++++++++++++++++++
thông tin cấu hình trên router NH-HCM
!
version 12.4
service timestamps log datetime msec
service timestamps debug datetime msec
service password-encryption
!
hostname NM-HCM
!
!
!
enable secret 5 $1$2Jwq$uMPQaFMmYb3yeqwhCs8Ut0
!
!
!
!
ip cef
no ipv6 cef
!
!
!
username admin secret 5 $1$f22E$3OqCWMxKJ9xBpwZv8db3r/
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp key saigonnhamay address 200.0.0.2
!
!
crypto ipsec security-association lifetime seconds 1800
!
crypto ipsec transform-set vpnset esp-des esp-md5-hmac
!
crypto map vpnmap 10 ipsec-isakmp
set peer 200.0.0.2
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
description "ket noi toi Lan NM-HCM"
ip address 192.168.4.254 255.255.255.0
duplex auto
speed auto
!
interface Serial0/0/0
description "ket noi toi ISP"
ip address 200.0.0.10 255.255.255.252
clock rate 2000000
crypto map vpnmap
!
interface Serial0/0/1
no ip address
clock rate 2000000
shutdown
!
interface Vlan1
no ip address
!
ip classless
ip route 0.0.0.0 0.0.0.0 200.0.0.9
!
ip flow-export version 9
!
!
access-list 100 permit ip 192.168.4.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login local
!
!
!
end
++++++++++++++++++++++++++++++++++++++
hiện tại em đã cấu hình thành công trên mô hình ảo packet tracer rồi vpn từ saigon => hanoi, saigon => nh-hcm
nhưng khi em triển khai thực tế thì chỉ được 1 site ping thấy nhau cùng một thời điểm nghĩa là saigon => hanoi hoặc saigon => nh-hcm
hiện tại router em dùng phiên bản: c1841-adventerprisek9-mz.151-2.T.bin không biết có được không em thấy trên cisco packet tracer dùng pb: c1841-advipservicesk9-mz.124-15.T1.bin
không biết là router 1841 có hỗ trợ multivpn không?
mong anh em cho em ý kiến
https://lh3.googleusercontent.com/zE...E=w711-h420-no
thông tin cấu hình router saigon
!
version 12.4
service timestamps log datetime msec
service timestamps debug datetime msec
no service password-encryption
!
hostname HCM-R
!
!
!
enable secret 5 $1$8Fwe$I.fE7fBzTMhqf6sr/Jx8g/
!
!
!
ip dhcp pool vlan10
network 192.168.1.0 255.255.255.192
default-router 192.168.1.62
ip dhcp pool vlan20
network 192.168.1.64 255.255.255.192
default-router 192.168.1.126
ip dhcp pool vlan30
network 192.168.1.128 255.255.255.224
default-router 192.168.1.158
ip dhcp pool vlan40
network 192.168.1.160 255.255.255.224
default-router 192.168.1.190
ip dhcp pool vlan50
network 192.168.1.192 255.255.255.240
default-router 192.168.1.206
!
ip cef
no ipv6 cef
!
!
!
username admin secret 5 $1$NZyN$NL5zMBfHeZXWu09g8za7Z.
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp key saigonhanoi address 200.0.0.6
crypto isakmp key saigonnhamay address 200.0.0.10
!
!
crypto ipsec security-association lifetime seconds 1800
!
crypto ipsec transform-set vpnset esp-des esp-md5-hmac
!
crypto map vpnmap 10 ipsec-isakmp
set peer 200.0.0.6
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
crypto map vpnmap 20 ipsec-isakmp
set peer 200.0.0.10
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/0.10
encapsulation dot1Q 10
ip address 192.168.1.62 255.255.255.192
!
interface FastEthernet0/0.20
encapsulation dot1Q 20
ip address 192.168.1.126 255.255.255.192
!
interface FastEthernet0/0.30
encapsulation dot1Q 30
ip address 192.168.1.158 255.255.255.224
!
interface FastEthernet0/0.40
encapsulation dot1Q 40
ip address 192.168.1.190 255.255.255.224
!
interface FastEthernet0/0.50
encapsulation dot1Q 50
ip address 192.168.1.206 255.255.255.240
!
interface FastEthernet0/1
description "ket noi toi ISP"
ip address 200.0.0.2 255.255.255.252
duplex auto
speed auto
crypto map vpnmap
!
interface Vlan1
no ip address
!
ip classless
ip route 0.0.0.0 0.0.0.0 200.0.0.1
!
ip flow-export version 9
!
!
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.4.0 0.0.0.255
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login local
!
!
!
end
++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++
thông tin cấu hình trên router hanoi
!
version 12.4
service timestamps log datetime msec
service timestamps debug datetime msec
service password-encryption
!
hostname HANOI
!
!
!
enable secret 5 $1$dqE5$uY4NBhtPEiLdHECR2IrDv.
!
!
!
ip dhcp pool vlan10
network 192.168.2.0 255.255.255.192
default-router 192.168.2.62
dns-server 192.168.2.161
ip dhcp pool vlan20
network 192.168.2.64 255.255.255.192
default-router 192.168.2.126
dns-server 192.168.2.161
ip dhcp pool vlan30
network 192.168.2.128 255.255.255.224
default-router 192.168.2.158
dns-server 192.168.2.161
ip dhcp pool vlan40
network 192.168.2.160 255.255.255.224
default-router 192.168.2.190
dns-server 192.168.2.161
ip dhcp pool vlan50
network 192.168.2.192 255.255.255.240
default-router 192.168.2.206
dns-server 192.168.2.161
!
ip cef
no ipv6 cef
!
!
!
username admin secret 5 $1$Blqb$NPsUIq4PINtKjeJR8AraO0
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp key saigonhanoi address 200.0.0.2
!
!
crypto ipsec security-association lifetime seconds 1800
!
crypto ipsec transform-set vpnset esp-des esp-md5-hmac
!
crypto map vpnmap 10 ipsec-isakmp
set peer 200.0.0.2
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
description "ket noi toi ISP"
ip address 200.0.0.6 255.255.255.252
duplex auto
speed auto
crypto map vpnmap
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.10
encapsulation dot1Q 10
ip address 192.168.2.62 255.255.255.192
!
interface FastEthernet0/1.20
encapsulation dot1Q 20
ip address 192.168.2.126 255.255.255.192
!
interface FastEthernet0/1.30
encapsulation dot1Q 30
ip address 192.168.2.158 255.255.255.224
!
interface FastEthernet0/1.40
encapsulation dot1Q 40
ip address 192.168.2.190 255.255.255.224
!
interface FastEthernet0/1.50
encapsulation dot1Q 50
ip address 192.168.2.206 255.255.255.240
!
interface Vlan1
no ip address
!
ip classless
ip route 0.0.0.0 0.0.0.0 200.0.0.9
ip route 0.0.0.0 0.0.0.0 200.0.0.5
!
ip flow-export version 9
!
!
access-list 100 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login local
!
!
!
end
+++++++++++++++++++++++++++++++++++++++++++++++
thông tin cấu hình trên router NH-HCM
!
version 12.4
service timestamps log datetime msec
service timestamps debug datetime msec
service password-encryption
!
hostname NM-HCM
!
!
!
enable secret 5 $1$2Jwq$uMPQaFMmYb3yeqwhCs8Ut0
!
!
!
!
ip cef
no ipv6 cef
!
!
!
username admin secret 5 $1$f22E$3OqCWMxKJ9xBpwZv8db3r/
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp key saigonnhamay address 200.0.0.2
!
!
crypto ipsec security-association lifetime seconds 1800
!
crypto ipsec transform-set vpnset esp-des esp-md5-hmac
!
crypto map vpnmap 10 ipsec-isakmp
set peer 200.0.0.2
set security-association lifetime seconds 1800
set transform-set vpnset
match address 100
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
description "ket noi toi Lan NM-HCM"
ip address 192.168.4.254 255.255.255.0
duplex auto
speed auto
!
interface Serial0/0/0
description "ket noi toi ISP"
ip address 200.0.0.10 255.255.255.252
clock rate 2000000
crypto map vpnmap
!
interface Serial0/0/1
no ip address
clock rate 2000000
shutdown
!
interface Vlan1
no ip address
!
ip classless
ip route 0.0.0.0 0.0.0.0 200.0.0.9
!
ip flow-export version 9
!
!
access-list 100 permit ip 192.168.4.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
!
line con 0
login local
!
line aux 0
!
line vty 0 4
login local
!
!
!
end
++++++++++++++++++++++++++++++++++++++
hiện tại em đã cấu hình thành công trên mô hình ảo packet tracer rồi vpn từ saigon => hanoi, saigon => nh-hcm
nhưng khi em triển khai thực tế thì chỉ được 1 site ping thấy nhau cùng một thời điểm nghĩa là saigon => hanoi hoặc saigon => nh-hcm
hiện tại router em dùng phiên bản: c1841-adventerprisek9-mz.151-2.T.bin không biết có được không em thấy trên cisco packet tracer dùng pb: c1841-advipservicesk9-mz.124-15.T1.bin
không biết là router 1841 có hỗ trợ multivpn không?
mong anh em cho em ý kiến

Comment