Question 1
What are three required steps to configure DHCP snooping on a switch? (Choose three)
A. Configure the switch to insert and remove DHCP relay information (option-82 field) in forwarded DHCP request messages.
B. Configure DHCP snooping globally.
C. Configure the switch as a DHCP server.
D. Configure DHCP snooping on an interface.
E. Configure all interfaces as DHCP snooping trusted interfaces.
F. Configure DHCP snooping on a VLAN or range of VLANs.
Answer: B D F
Explanation
To configure DHCP snooping feature, at least three steps must be done:
Other steps are just optional:
+ Configure DHCP Option 82
Switch(config)# ip dhcp snooping information option
+ Configure the number of DHCP packets per second (pps) that are acceptable on the port:
Switch(config-if)# ip dhcp snooping limit rate {rate}
Question 2
Which statement is true about DHCP spoofing operation?
A. DHCP spoofing and SPAN cannot be used on the same port of a switch.
B. To prevent a DHCP spoofing, the DHCP server must create a static ARP entry that cannot be updated by a dynamic ARP packet.
C. To prevent a DHCP spoofing, the switch must have DHCP server services disabled and a static entry pointing towards the DHCP server.
D. DHCP spoofing can be prevented by placing all unused ports in an unused VLAN.
Answer: B
Explanation
First let’s analyze answer A.
Switched Port Analyzer (SPAN) feature copies network traffic from a VLAN or group of ports to a selected port. SPAN is generally referred to as Port mirroring. An example of configuring SPAN port is shown below:
The above configuration will capture all traffic from interface FastEthernet 0/1 and send it to interface FastEthernet 0/2.
Answer A is a bit unclear because SPAN involves 2 ports: source and destination ports; but we don’t know which port is mentioned. SPAN does not affect the switching function on the source port but it does affect the destination port: all incoming traffic is disable on destination port so DHCP spoofing cannot be done on this port. I suppose this question wants to mention about source port, which makes answer A incorrect.
Although it is not mentioned in the books but answer B is the best choice. If the DHCP server can create a static ARP entry that cannot be updated by a dynamic ARP packet then the attacker cannot change the MAC address information of the DHCP server on client -> B is correct.
Usually a switch does not have DHCP server services; also a static entry pointing towards the DHCP server will not help prevent DHCP spoofing -> C is not correct.
Place all unused ports in an unused VLAN can prevent VLAN Hopping, not DHCP spoofing -> D is not correct.
Question 3
Refer to the exhibit. What type of attack is being defended against?

A. Snooping attack
B. Rogue device attack
C. STP attack
D. VLAN attack
E. Spoofing attack
F. MAC flooding attack
Answer: E
Explanation
DHCP snooping is a method used to defend DHCP spoofing.
Question 4
An attacker is launching a DoS attack with a public domain hacking tool that is used to exhaust the IP address space available from the DHCP servers for a period of time. Which procedure would best defend against this type of attack?
A. Configure only trusted interfaces with root guard.
B. Implement private VLANs (PVLANs) to carry only user traffic.
C. Implement private VLANs (PVLANs) to carry only DHCP traffic.
D. Configure only untrusted interfaces with root guard.
E. Configure DHCP spoofing on all ports that connect untrusted clients.
F. Configure DHCP snooping only on ports that connect trusted DHCP servers.
Answer: F
Explanation
To defend DHCP spoofing attack, we only need to configure DHCP snooping on trusted interfaces because other ports are classified as untrusted ports by default.
Question 5
Refer to the exhibit. DHCP snooping is enabled for selected VLANs to provide security on the network. How do the switch ports handle the DHCP messages?
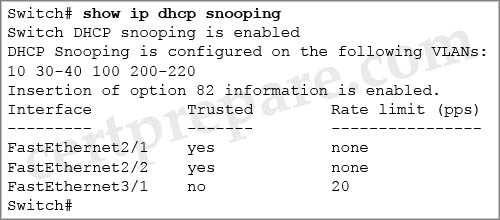
A. Ports Fa2/1 and Fa2/2 source DHCP requests only. Port Fa3/1 is eligible to source all DHCP messages and respond to DHCP requests.
B. Ports Fa2/1 and Fa2/2 respond to DHCP requests only. Port Fa3/1 is eligible to source all DHCP messages.
C. Ports Fa2/1 and Fa2/2 are eligible to source all DHCP messages and respond to DHCP requests. Port Fa3/1 can source DHCP requests only.
D. All three ports, Fa2/1, Fa2/2, and Fa3/1, are eligible to source all DHCP messages and respond to DHCP requests.
Answer: C
Explanation
Trusted ports are allowed to send all types of DHCP messages. Untrusted ports can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down. In this case, Fa2/1 & Fa2/2 are trusted (can send all types of DHCP messages) while Fa3/1 is untrusted (can only send DHCP requests).
Question 6
Refer to the exhibit. An attacker is connected to interface Fa0/11 on switch A-SW2 and attempts to establish a DHCP server for a man-in-middle attack. Which recommendation, if followed, would mitigate this type of attack?
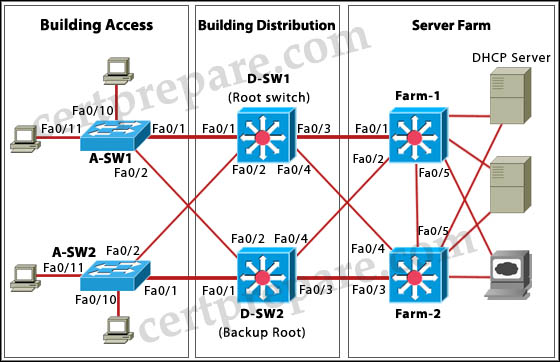 A. All switch ports in the Building Access block should be configured as DHCP untrusted ports.
A. All switch ports in the Building Access block should be configured as DHCP untrusted ports.
B. All switch ports in the Building Access block should be configured as DHCP trusted ports.
C. All switch ports connecting to servers in the Server Farm block should be configured as DHCP untrusted ports.
D. All switch ports connecting to hosts in the Building Access block should be configured as DHCP trusted ports.
E. All switch ports in the Server Farm block should be configured as DHCP untrusted ports.
F. All switch ports connecting to hosts in the Building Access block should be configured as DHCP untrusted ports.
Answer: F
Explanation
All switch ports connecting to hosts should only send DHCP Requests and they are the ports that can be easily accessed by an attacker -> They should be configured as DHCP untrusted ports.
Question 7
Refer to the exhibit.
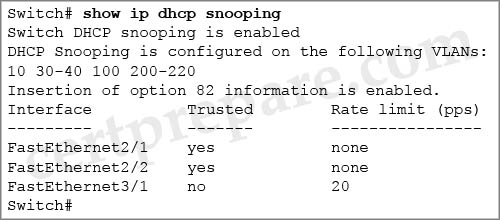
DHCP snooping is enabled for selected VLANs to provide security on the network. How do the switch ports handle the DHCP messages?
A. A DHCPOFFER packet from a DHCP seiver received on Ports Fa2/1 and Fa2/2 is dropped.
B. A DHCP packet received on ports Fa2/1 and Fa2/2 is dropped if the source MAC address and the DHCP client hardware address does not match Snooping database.
C. A DHCP packet received on ports Fa2/1 and Fa2/2 is forwarded without being tested.
D. A DHCPRELEASE message received on ports Fa2/1 and Fa2/2 has a MAC address in the DHCP snooping binding database, but the interface information in the binding database does not match the interface on which the message was received and is dropped.
Answer: C
Explanation
Interface Fa2/1 & 2/2 have been configured as trusted ports so packets received on these interfaces are forwarded without being tested.
What are three required steps to configure DHCP snooping on a switch? (Choose three)
A. Configure the switch to insert and remove DHCP relay information (option-82 field) in forwarded DHCP request messages.
B. Configure DHCP snooping globally.
C. Configure the switch as a DHCP server.
D. Configure DHCP snooping on an interface.
E. Configure all interfaces as DHCP snooping trusted interfaces.
F. Configure DHCP snooping on a VLAN or range of VLANs.
Answer: B D F
Explanation
To configure DHCP snooping feature, at least three steps must be done:
| Sequence and Description | Command |
| 1. Configure global DHCP snooping | Switch(config)# ip dhcp snooping |
| 2. Configure trusted ports (as least on 1 port). By default, all ports are untrusted |
Switch(config-if)# ip dhcp snooping trust |
| 3. Configure DHCP snooping for the selected VLANs | Switch(config)# ip dhcp snooping vlan {VLAN-ID | VLAN range} |
+ Configure DHCP Option 82
Switch(config)# ip dhcp snooping information option
+ Configure the number of DHCP packets per second (pps) that are acceptable on the port:
Switch(config-if)# ip dhcp snooping limit rate {rate}
Question 2
Which statement is true about DHCP spoofing operation?
A. DHCP spoofing and SPAN cannot be used on the same port of a switch.
B. To prevent a DHCP spoofing, the DHCP server must create a static ARP entry that cannot be updated by a dynamic ARP packet.
C. To prevent a DHCP spoofing, the switch must have DHCP server services disabled and a static entry pointing towards the DHCP server.
D. DHCP spoofing can be prevented by placing all unused ports in an unused VLAN.
Answer: B
Explanation
First let’s analyze answer A.
Switched Port Analyzer (SPAN) feature copies network traffic from a VLAN or group of ports to a selected port. SPAN is generally referred to as Port mirroring. An example of configuring SPAN port is shown below:
| Switch(config)#monitor session 1 source interface FastEthernet 0/1 Switch(config)#monitor session 1 destination interface FastEthernet 0/2 |
Answer A is a bit unclear because SPAN involves 2 ports: source and destination ports; but we don’t know which port is mentioned. SPAN does not affect the switching function on the source port but it does affect the destination port: all incoming traffic is disable on destination port so DHCP spoofing cannot be done on this port. I suppose this question wants to mention about source port, which makes answer A incorrect.
Although it is not mentioned in the books but answer B is the best choice. If the DHCP server can create a static ARP entry that cannot be updated by a dynamic ARP packet then the attacker cannot change the MAC address information of the DHCP server on client -> B is correct.
Usually a switch does not have DHCP server services; also a static entry pointing towards the DHCP server will not help prevent DHCP spoofing -> C is not correct.
Place all unused ports in an unused VLAN can prevent VLAN Hopping, not DHCP spoofing -> D is not correct.
Question 3
Refer to the exhibit. What type of attack is being defended against?

A. Snooping attack
B. Rogue device attack
C. STP attack
D. VLAN attack
E. Spoofing attack
F. MAC flooding attack
Answer: E
Explanation
DHCP snooping is a method used to defend DHCP spoofing.
Question 4
An attacker is launching a DoS attack with a public domain hacking tool that is used to exhaust the IP address space available from the DHCP servers for a period of time. Which procedure would best defend against this type of attack?
A. Configure only trusted interfaces with root guard.
B. Implement private VLANs (PVLANs) to carry only user traffic.
C. Implement private VLANs (PVLANs) to carry only DHCP traffic.
D. Configure only untrusted interfaces with root guard.
E. Configure DHCP spoofing on all ports that connect untrusted clients.
F. Configure DHCP snooping only on ports that connect trusted DHCP servers.
Answer: F
Explanation
To defend DHCP spoofing attack, we only need to configure DHCP snooping on trusted interfaces because other ports are classified as untrusted ports by default.
Question 5
Refer to the exhibit. DHCP snooping is enabled for selected VLANs to provide security on the network. How do the switch ports handle the DHCP messages?

A. Ports Fa2/1 and Fa2/2 source DHCP requests only. Port Fa3/1 is eligible to source all DHCP messages and respond to DHCP requests.
B. Ports Fa2/1 and Fa2/2 respond to DHCP requests only. Port Fa3/1 is eligible to source all DHCP messages.
C. Ports Fa2/1 and Fa2/2 are eligible to source all DHCP messages and respond to DHCP requests. Port Fa3/1 can source DHCP requests only.
D. All three ports, Fa2/1, Fa2/2, and Fa3/1, are eligible to source all DHCP messages and respond to DHCP requests.
Answer: C
Explanation
Trusted ports are allowed to send all types of DHCP messages. Untrusted ports can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down. In this case, Fa2/1 & Fa2/2 are trusted (can send all types of DHCP messages) while Fa3/1 is untrusted (can only send DHCP requests).
Question 6
Refer to the exhibit. An attacker is connected to interface Fa0/11 on switch A-SW2 and attempts to establish a DHCP server for a man-in-middle attack. Which recommendation, if followed, would mitigate this type of attack?

B. All switch ports in the Building Access block should be configured as DHCP trusted ports.
C. All switch ports connecting to servers in the Server Farm block should be configured as DHCP untrusted ports.
D. All switch ports connecting to hosts in the Building Access block should be configured as DHCP trusted ports.
E. All switch ports in the Server Farm block should be configured as DHCP untrusted ports.
F. All switch ports connecting to hosts in the Building Access block should be configured as DHCP untrusted ports.
Answer: F
Explanation
All switch ports connecting to hosts should only send DHCP Requests and they are the ports that can be easily accessed by an attacker -> They should be configured as DHCP untrusted ports.
Question 7
Refer to the exhibit.

DHCP snooping is enabled for selected VLANs to provide security on the network. How do the switch ports handle the DHCP messages?
A. A DHCPOFFER packet from a DHCP seiver received on Ports Fa2/1 and Fa2/2 is dropped.
B. A DHCP packet received on ports Fa2/1 and Fa2/2 is dropped if the source MAC address and the DHCP client hardware address does not match Snooping database.
C. A DHCP packet received on ports Fa2/1 and Fa2/2 is forwarded without being tested.
D. A DHCPRELEASE message received on ports Fa2/1 and Fa2/2 has a MAC address in the DHCP snooping binding database, but the interface information in the binding database does not match the interface on which the message was received and is dropped.
Answer: C
Explanation
Interface Fa2/1 & 2/2 have been configured as trusted ports so packets received on these interfaces are forwarded without being tested.
